Do you trust your messaging app even though it uses end-to-end encryption?
As I previously said end-to-end encryption doesn't mean that your messages are secure enough to hide your trace.
It's because most of the messaging apps still record and store a lot of metadata on your calls and messages that could reveal some of your personal information including dates and durations of communication, as well as the participants' phone numbers.
Apple's iMessage app is the most recent and best example of this scenario. Just recently it was reported that the company stores a lot of information about its end-to-end encrypted iMessage, that could reveal your contacts and location, and even share this data with law enforcement via court orders.
But if you are using open source end-to-end encrypted Signal app, you are on the safer side. Trust me!
As we previously reported that the Signal app, which is widely considered the most secure of all other encrypted messaging apps, stores minimum information about its users.
This was just recently proved when the app was put to the test earlier this year when an FBI subpoena and gag order demanded a wide range of information on two Signal users, but the authorities got their hands on information that's less or no use in the investigation.
Open Whisper Systems, the makers of Signal, revealed Tuesday that the company had received a federal subpoena earlier this year for records and other details on two of its users as part of a federal grand jury investigation in Virginia.
But unfortunately for the government, Signal keeps as little data as possible on its users, and therefore Open Whisper Systems was unable to hand over anything useful to the FBI agents that could help them in their investigation.
Here's what the FBI demanded on the two suspects, seeking a subpoena:
And here's what the company turned over to the FBI:
Much information about the subpoena is still secret — including the case number, the date the subpoena was served, and other details of the underlying case — but it's very much clear that the FBI sought detailed information on two suspects who used Signal app.
Open Whisper Systems is also the force behind the Signal Protocol that powers the encryption built into WhatsApp, Facebook Messenger, and Google Allo's Incognito mode.
As I previously said end-to-end encryption doesn't mean that your messages are secure enough to hide your trace.
It's because most of the messaging apps still record and store a lot of metadata on your calls and messages that could reveal some of your personal information including dates and durations of communication, as well as the participants' phone numbers.
Apple's iMessage app is the most recent and best example of this scenario. Just recently it was reported that the company stores a lot of information about its end-to-end encrypted iMessage, that could reveal your contacts and location, and even share this data with law enforcement via court orders.
But if you are using open source end-to-end encrypted Signal app, you are on the safer side. Trust me!
As we previously reported that the Signal app, which is widely considered the most secure of all other encrypted messaging apps, stores minimum information about its users.
This was just recently proved when the app was put to the test earlier this year when an FBI subpoena and gag order demanded a wide range of information on two Signal users, but the authorities got their hands on information that's less or no use in the investigation.
Open Whisper Systems, the makers of Signal, revealed Tuesday that the company had received a federal subpoena earlier this year for records and other details on two of its users as part of a federal grand jury investigation in Virginia.
But unfortunately for the government, Signal keeps as little data as possible on its users, and therefore Open Whisper Systems was unable to hand over anything useful to the FBI agents that could help them in their investigation.
Here's what the FBI demanded on the two suspects, seeking a subpoena:
- Subscriber name
- Payment information
- Associated IP addresses
- Email addresses
- History logs
- Browser cookie data
- Other information associated with two phone numbers
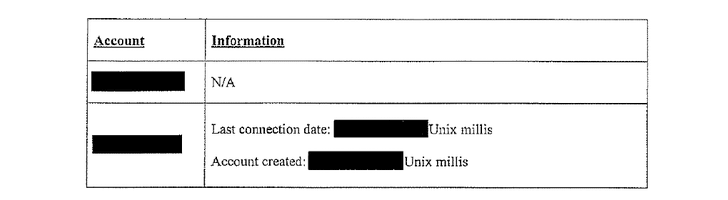
And here's what the company turned over to the FBI:
"As the documents show, the government's effort did not amount to much—not because OWS refused to comply with the government's subpoena (it complied), but because the company simply does not keep the kinds of information about their customers that the government sought (and that too many technology companies continue to amass)," the ACLU said in a post. "All OWS was able to provide were the dates and times for when the account was created and when it last connected to Signal's servers."You can see a number of court filings related to the subpoena published by the American Civil Liberties Union (ACLU), which is representing Open Whisper Systems in the fight.
Much information about the subpoena is still secret — including the case number, the date the subpoena was served, and other details of the underlying case — but it's very much clear that the FBI sought detailed information on two suspects who used Signal app.
Open Whisper Systems is also the force behind the Signal Protocol that powers the encryption built into WhatsApp, Facebook Messenger, and Google Allo's Incognito mode.
Have something to say about this article? Comment below or share it with us on Facebook, Twitter or our LinkedIn Group.