Cybercrime has continued to evolve and today exists in a highly organised form.
Cybercrime has increasingly been commercialised, and itself become big business by renting out an expanded range of hacking tools and technologies, from exploit kits to ransomware, to help anyone build threats and launch attacks.
In past few years, we have witnessed the increase in the popularity of malware-as-a-service (MaaS), which is today a prosperous business on the underground black market that offers an array of services, including ransomware-as-a-service, DDoS-as-a-service, phishing-as-a-service, and much more.
Two such services have recently been spotted by two separate group of researchers, which we have detailed in this article.
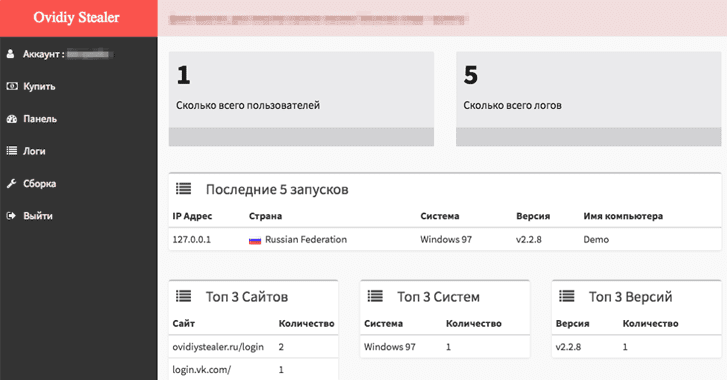
Dubbed Ovidiy Stealer, the malware was initially appeared just last month but is being regularly updated by its Russian-speaking authors and actively adopted by cyber criminals.
The Ovidiy Stealer malware currently has several versions in the wild, targeting people around the world, including the United Kingdom, the Netherlands, India, and Russia, according to security researchers at Proofpoint, who analysed the malware.
What's surprising is the Ovidiy Stealer's cost.
A single customizable build of this lightweight, easy-to-use, and effective malware product only costs between 450 and 750 Rubles (nearly $7 and $13), according to security researchers at Proofpoint, who uncovered and analysed the malware.
Despite its low price, the malware build executables are encrypted, which make them difficult to detect and analyse, though the report also notes that some antivirus products are detecting Ovidiy Stealer with its behaviour.
Written in .NET, the credentials stealer malware comes with the ability to target multiple applications and browsers, including Google Chrome, Opera, FileZilla, Amigo, Kometa, Torch, and Orbitum, but buyers can purchase a version that only works on a single browser.
The malware is being distributed via a number of methods, including malicious email attachments, malicious links to a download, fake software or tools offered on various file-hosting websites, and even within software packages.
Ovidiy Stealer itself is not very powerful and advanced, as it does not include any persistence mechanism that allows the malware to run after a reboot, but it has the potential to become widespread.
Ovidiy Stealer uses SSL/TLS connection for secure communication with the command and control server, which is hosted on a Russian domain — the same domain used to market and sell the malware.
Dubbed Hackshit, the PhaaS platform attracts new subscribers by offering them free trial accounts to review their limited set of hacking tutorials and tricks to make easy money.
Researchers noted that the phishing pages use data URI scheme to serve base64 encoded content from "a secure HTTPS websites with ".moe" top level domain (TLD) to evade traditional scanners."
These crimeware-as-a-service poses a new security challenge because it not only allows malicious actors to leverage other cybercriminals' resources to conduct attacks, but also bringing wannabe hackers into the world of cybercrime.
Cybercrime has increasingly been commercialised, and itself become big business by renting out an expanded range of hacking tools and technologies, from exploit kits to ransomware, to help anyone build threats and launch attacks.
In past few years, we have witnessed the increase in the popularity of malware-as-a-service (MaaS), which is today a prosperous business on the underground black market that offers an array of services, including ransomware-as-a-service, DDoS-as-a-service, phishing-as-a-service, and much more.
Two such services have recently been spotted by two separate group of researchers, which we have detailed in this article.
Ovidiy Stealer — $7 Password-Stealing Malware For Everyone
A new credential stealing malware that targets primarily web browsers is being marketed at Russian-speaking web forums for as cheap as $7, allowing anyone with even little technical knowledge to hack as many computers as they want.Dubbed Ovidiy Stealer, the malware was initially appeared just last month but is being regularly updated by its Russian-speaking authors and actively adopted by cyber criminals.
The Ovidiy Stealer malware currently has several versions in the wild, targeting people around the world, including the United Kingdom, the Netherlands, India, and Russia, according to security researchers at Proofpoint, who analysed the malware.
What's surprising is the Ovidiy Stealer's cost.
A single customizable build of this lightweight, easy-to-use, and effective malware product only costs between 450 and 750 Rubles (nearly $7 and $13), according to security researchers at Proofpoint, who uncovered and analysed the malware.
Despite its low price, the malware build executables are encrypted, which make them difficult to detect and analyse, though the report also notes that some antivirus products are detecting Ovidiy Stealer with its behaviour.
Written in .NET, the credentials stealer malware comes with the ability to target multiple applications and browsers, including Google Chrome, Opera, FileZilla, Amigo, Kometa, Torch, and Orbitum, but buyers can purchase a version that only works on a single browser.
The malware is being distributed via a number of methods, including malicious email attachments, malicious links to a download, fake software or tools offered on various file-hosting websites, and even within software packages.
Ovidiy Stealer itself is not very powerful and advanced, as it does not include any persistence mechanism that allows the malware to run after a reboot, but it has the potential to become widespread.
Ovidiy Stealer uses SSL/TLS connection for secure communication with the command and control server, which is hosted on a Russian domain — the same domain used to market and sell the malware.
"A lightweight, easy-to-use, and effective product coupled with frequent updates and a stable support system give Ovidiy Stealer the potential to become a much more widespread threat," the report concluded.
"Ovidiy Stealer highlights the manner in the cybercrime marketplace drives innovation and new entrants and challenges organisations that must keep pace with the latest threats to their users, their data, and their systems."
Hackshit — Easier Phishing Than Ever Before!
Another crimeware-as-a-service uncovered by researchers from Netskope Threat Research Labs detailed a Phishing-as-a-Service (PhaaS) platform that offers low cost, "automated solution for the beginner scammers," allowing them to trick people into handing over their credentials.Dubbed Hackshit, the PhaaS platform attracts new subscribers by offering them free trial accounts to review their limited set of hacking tutorials and tricks to make easy money.
"The marketplace is a portal that offers services to purchase and sell for carrying out the phishing attacks," Netskope researcher Ashwin Vamshi says.
"The attacker then generates a phished page from the page/generator link and logs into the email account of the compromised victim, views all the contacts and sends an email embedded with the phished link."Hackshit allows wannabe hackers (subscribers) to generate their unique phishing pages for several services, including Yahoo, Facebook, and Google's Gmail.
Researchers noted that the phishing pages use data URI scheme to serve base64 encoded content from "a secure HTTPS websites with ".moe" top level domain (TLD) to evade traditional scanners."
"Based on one of the video tutorials we observed, the attacker purchases site login accounts of compromised victim from the marketplace using Perfect Money or bitcoins," the researcher says.Moreover, Hackshit website is using an SSL certificate issued by Let's Encrypt — the open certificate authority (CA) that offers free SSL/TLS (Secure Socket Layer/Transport Layer Security) certificates for web servers, making HTTPS implementation easier for everyone.
These crimeware-as-a-service poses a new security challenge because it not only allows malicious actors to leverage other cybercriminals' resources to conduct attacks, but also bringing wannabe hackers into the world of cybercrime.
Have something to say about this article? Comment below or share it with us on Facebook, Twitter or our LinkedIn Group.