Nearly a year after the disclosure of the Dirty COW vulnerability that affected the Linux kernel, cybercriminals have started exploiting the vulnerability against Android users, researchers have warned.
Publicly disclosed last year in October, Dirty COW was present in a section of the Linux kernel—a part of virtually every Linux distribution, including Red Hat, Debian, and Ubuntu—for years and was actively exploited in the wild.
The vulnerability allows an unprivileged local attacker to gain root access through a race condition issue, gain access to read-only root-owned executable files, and permit remote attacks.
However, security researchers from Trend Micro published a blog post on Monday disclosing that the privilege escalation vulnerability (CVE-2016-5195), known as Dirty COW, has now been actively exploited by a malware sample of ZNIU, detected as AndroidOS_ZNIU.
This is the first time we have seen a malware sample to contain an exploit for the vulnerability designed to compromise devices running on the mobile platform.
The malware uses the Dirty COW exploit to root Android devices via the copy-on-write (COW) mechanism in Android's Linux kernel and install a backdoor which can then be used by attackers to collect data and generate profit through a premium rate phone number.
Trend Micro researchers detected the ZNIU malware in more than 1,200 malicious Android apps—some of which disguised themselves as pornography and gaming apps—alongside host websites containing malware rootkits that exploit Dirty Cow.
While the Dirty Cow flaw impacts all versions of the Android operating system, the ZNIU's Dirty Cow exploit only affects Android devices with ARM/X86 64-bit architecture. However, the recent exploit can be used to bypass SELinux and plant backdoors.
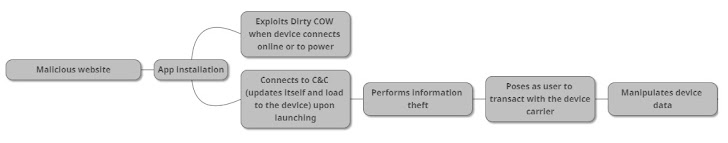
Once downloaded and installed, the ZNIU malware-carrying app communicates with its command-and-control (C&C) server to check for code updates, while simultaneously the Dirty Cow exploit provides local privilege escalation to gain root access on the device, bypass system restrictions and "plant a backdoor for potential remote control attacks in the future."
The malware also harvests the carrier information of the user and attempts to send payments via premium SMS messages that were directed to a dummy company in China.
Once the SMS transaction is over, the malware also deletes the messages from the device in order to erase evidence of any compromise.
The researchers found the malware has already infected more than 5,000 Android users across 40 countries in recent weeks, with the majority of victims found in China and India, while other resides in the United States, Japan, Canada, Germany and Indonesia.
Google has released an update for Android that, among other fixes, officially fixes the Dirty COW vulnerability. The tech giant also confirmed that its Play Protect now protects Android users against this malware.
The easiest way to prevent yourself from being targeted by such clever malware is to avoid downloading apps from third-party sources and always stick to the official Google Play Store.
Publicly disclosed last year in October, Dirty COW was present in a section of the Linux kernel—a part of virtually every Linux distribution, including Red Hat, Debian, and Ubuntu—for years and was actively exploited in the wild.
The vulnerability allows an unprivileged local attacker to gain root access through a race condition issue, gain access to read-only root-owned executable files, and permit remote attacks.
However, security researchers from Trend Micro published a blog post on Monday disclosing that the privilege escalation vulnerability (CVE-2016-5195), known as Dirty COW, has now been actively exploited by a malware sample of ZNIU, detected as AndroidOS_ZNIU.
This is the first time we have seen a malware sample to contain an exploit for the vulnerability designed to compromise devices running on the mobile platform.
This Dirty Cow Exploit found in Over 1,200 Android Apps
The malware uses the Dirty COW exploit to root Android devices via the copy-on-write (COW) mechanism in Android's Linux kernel and install a backdoor which can then be used by attackers to collect data and generate profit through a premium rate phone number.
Trend Micro researchers detected the ZNIU malware in more than 1,200 malicious Android apps—some of which disguised themselves as pornography and gaming apps—alongside host websites containing malware rootkits that exploit Dirty Cow.
While the Dirty Cow flaw impacts all versions of the Android operating system, the ZNIU's Dirty Cow exploit only affects Android devices with ARM/X86 64-bit architecture. However, the recent exploit can be used to bypass SELinux and plant backdoors.
"We monitored six ZNIU rootkits, four of which were Dirty COW exploits. The other two were KingoRoot, a rooting app, and the Iovyroot exploit (CVE-2015-1805)," the researchers said.
"ZNIU used KingoRoot and Iovyroot because they can root ARM 32-bit CPU devices, which the rootkit for Dirty COW cannot."
Here's How the ZNIU's Dirty Cow exploit Works
Once downloaded and installed, the ZNIU malware-carrying app communicates with its command-and-control (C&C) server to check for code updates, while simultaneously the Dirty Cow exploit provides local privilege escalation to gain root access on the device, bypass system restrictions and "plant a backdoor for potential remote control attacks in the future."
The malware also harvests the carrier information of the user and attempts to send payments via premium SMS messages that were directed to a dummy company in China.
Once the SMS transaction is over, the malware also deletes the messages from the device in order to erase evidence of any compromise.
The researchers found the malware has already infected more than 5,000 Android users across 40 countries in recent weeks, with the majority of victims found in China and India, while other resides in the United States, Japan, Canada, Germany and Indonesia.
Google has released an update for Android that, among other fixes, officially fixes the Dirty COW vulnerability. The tech giant also confirmed that its Play Protect now protects Android users against this malware.
The easiest way to prevent yourself from being targeted by such clever malware is to avoid downloading apps from third-party sources and always stick to the official Google Play Store.
Have something to say about this article? Comment below or share it with us on Facebook, Twitter or our LinkedIn Group.