Beware, If you are using S/MIME protocol over Microsoft Outlook to encrypt your email communication, you need to watch out.
From at least last 6 months, your messages were being sent in both encrypted and unencrypted forms, exposing all your secret and sensitive communications to potential eavesdroppers.
S/MIME, or Secure/Multipurpose Internet Mail Extensions, is an end-to-end encryption protocol—based on public-key cryptography and works just like SSL connections—that enables users to send digitally signed and encrypted messages.
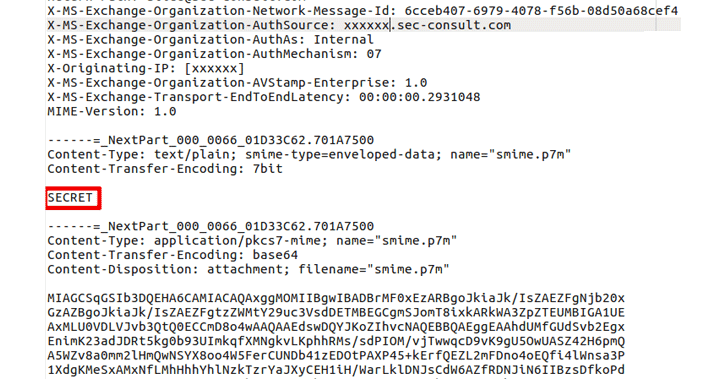
According to a security advisory published by SEC Consult earlier this week, a severe bug (CVE-2017-11776) in Microsoft Outlook email client causes S/MIME encrypted emails to be sent with their unencrypted versions attached.
When Outlook users make use of S/MIME to encrypt their messages and format their emails as plain text, the vulnerability allows the seemingly encrypted emails to be sent in both encrypted as well as human-readable clear text forms, the researchers explain.
Users would be unaware of this security issue, as the messages would appear as encrypted in the Outlook application's "Sent Items" folder.
Therefore, attackers with access to the unencrypted server-to-server or client-to-server connections could easily take advantage of this vulnerability to read the email communications in the plain text.
So if you used Outlook's S/MIME encryption for emails in the past 6 months, your emails have not been encrypted at all; instead, they went out in plain text.
According to the researchers, the scope of the vulnerability depends on how you have Outlook configured.
1. Outlook with Exchange (Impact limited to the first hop)
If you are using Outlook with Exchange, the plain text version of the encrypted emails will only reach one hop (to the sender's exchange), as sending emails to external exchange remove the plaintext part from the message.
But if the recipient and sender are in the same domain (exchange), the plain text part will be forwarded to the recipient as well.
2. Outlook using SMTP (Impact on the entire mail path)
If you are running Outlook with SMTP, the plain text version of the encrypted emails will not only be received by the recipient but also by all mail servers along the path.
Security researcher Kevin Beaumont independently verified the authenticity of the vulnerability, tweeting "Outlook S/MIME bug is absolutely reproducible, I just did it. Does not need an attacker. Microsoft has classified it wrong."
SEC researchers discovered the issue in May and responsibly reported it to Microsoft, but did not hear back from the tech giant.
Microsoft released a patch to fix the bug in this month's release of security updates, and rated the issue as "important," claiming the exploitation of this vulnerability was "unlikely" in the wild.
So, if you use Outlook's S/MIME for encrypting your sensitive emails, you are advised to patch your system and software as soon as possible.
From at least last 6 months, your messages were being sent in both encrypted and unencrypted forms, exposing all your secret and sensitive communications to potential eavesdroppers.
S/MIME, or Secure/Multipurpose Internet Mail Extensions, is an end-to-end encryption protocol—based on public-key cryptography and works just like SSL connections—that enables users to send digitally signed and encrypted messages.
According to a security advisory published by SEC Consult earlier this week, a severe bug (CVE-2017-11776) in Microsoft Outlook email client causes S/MIME encrypted emails to be sent with their unencrypted versions attached.
When Outlook users make use of S/MIME to encrypt their messages and format their emails as plain text, the vulnerability allows the seemingly encrypted emails to be sent in both encrypted as well as human-readable clear text forms, the researchers explain.
Users would be unaware of this security issue, as the messages would appear as encrypted in the Outlook application's "Sent Items" folder.
"To trigger the vulnerability, no active involvement by an attacker is required. An attacker might remain completely passive," the advisory reads.
"The impact is that a supposedly S/MIME encrypted mail can be read without the private keys of the recipient. This results in total loss of security properties provided by S/MIME encryption."
Therefore, attackers with access to the unencrypted server-to-server or client-to-server connections could easily take advantage of this vulnerability to read the email communications in the plain text.
So if you used Outlook's S/MIME encryption for emails in the past 6 months, your emails have not been encrypted at all; instead, they went out in plain text.
According to the researchers, the scope of the vulnerability depends on how you have Outlook configured.
1. Outlook with Exchange (Impact limited to the first hop)
If you are using Outlook with Exchange, the plain text version of the encrypted emails will only reach one hop (to the sender's exchange), as sending emails to external exchange remove the plaintext part from the message.
But if the recipient and sender are in the same domain (exchange), the plain text part will be forwarded to the recipient as well.
2. Outlook using SMTP (Impact on the entire mail path)
If you are running Outlook with SMTP, the plain text version of the encrypted emails will not only be received by the recipient but also by all mail servers along the path.
Security researcher Kevin Beaumont independently verified the authenticity of the vulnerability, tweeting "Outlook S/MIME bug is absolutely reproducible, I just did it. Does not need an attacker. Microsoft has classified it wrong."
Patch Outlook & Other Critical Windows Vulnerabilities
SEC researchers discovered the issue in May and responsibly reported it to Microsoft, but did not hear back from the tech giant.
Microsoft released a patch to fix the bug in this month's release of security updates, and rated the issue as "important," claiming the exploitation of this vulnerability was "unlikely" in the wild.
So, if you use Outlook's S/MIME for encrypting your sensitive emails, you are advised to patch your system and software as soon as possible.
Have something to say about this article? Comment below or share it with us on Facebook, Twitter or our LinkedIn Group.