Security researchers have discovered and disclosed details of two unpatched critical vulnerabilities in a popular internet forum software—vBulletin—one of which could allow a remote attacker to execute malicious code on the latest version of vBulletin application server.
vBulletin is a widely used proprietary Internet forum software package based on PHP and MySQL database server. It powers more than 100,000 websites on the Internet, including Fortune 500 and Alexa Top 1 million companies websites and forums.
The vulnerabilities were discovered by a security researcher from Italy-based security firm TRUEL IT and an unknown independent security researcher, who disclosed the details of the vulnerabilities by Beyond Security's SecuriTeam Secure Disclosure program.
The vulnerabilities affect version 5 of the vBulletin forum software and are currently unpatched. Beyond Security claims, it tried to contact vBulletin since November 21, 2017, but received no response from the company.
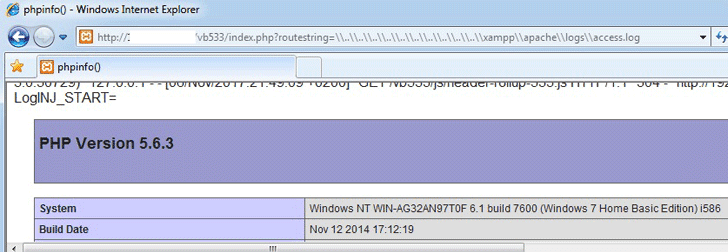
An unauthenticated attacker can trigger the file inclusion vulnerability by sending a GET request to index.php with the routestring= parameter in the request, eventually allowing the attacker to "create a crafted request to Vbulletin server installed on Windows OS and include any file on the web server."
The researcher has also provided Proof-of-Concept (PoC) exploit code to show the exploitation of the vulnerability. A Common Vulnerabilities and Exposures (CVE) number has not been assigned to this particular vulnerability.
The second vulnerability discovered in the vBulletin forum software version 5 has been assigned CVE-2017-17672 and described as a deserialization issue that an unauthenticated attacker can exploit to delete arbitrary files and even execute malicious code "under certain circumstances."
The vulnerability is due to unsafe usage of PHP's unserialize() on user-supplied input, which allows an unauthenticated hacker to delete arbitrary files and possibly execute arbitrary code on a vBulletin installation.
A publicly exposed API, called vB_Library_Template's cacheTemplates() function, allows fetching information on a set of given templates from the database to store them inside a cache variable.
We expect the vendor to release the patch for both the security flaws before hackers started exploiting them to target vBulletin installations.
vBulletin is a widely used proprietary Internet forum software package based on PHP and MySQL database server. It powers more than 100,000 websites on the Internet, including Fortune 500 and Alexa Top 1 million companies websites and forums.
The vulnerabilities were discovered by a security researcher from Italy-based security firm TRUEL IT and an unknown independent security researcher, who disclosed the details of the vulnerabilities by Beyond Security's SecuriTeam Secure Disclosure program.
The vulnerabilities affect version 5 of the vBulletin forum software and are currently unpatched. Beyond Security claims, it tried to contact vBulletin since November 21, 2017, but received no response from the company.
vBulletin Remote Code Execution Vulnerability
The first vulnerability discovered in vBulletin is a file inclusion issue that leads to remote code execution, allowing a remote attacker to include any file from the vBulletin server and execute arbitrary PHP code.An unauthenticated attacker can trigger the file inclusion vulnerability by sending a GET request to index.php with the routestring= parameter in the request, eventually allowing the attacker to "create a crafted request to Vbulletin server installed on Windows OS and include any file on the web server."
The researcher has also provided Proof-of-Concept (PoC) exploit code to show the exploitation of the vulnerability. A Common Vulnerabilities and Exposures (CVE) number has not been assigned to this particular vulnerability.
vBulletin Remote Arbitrary File Deletion Vulnerability
The second vulnerability discovered in the vBulletin forum software version 5 has been assigned CVE-2017-17672 and described as a deserialization issue that an unauthenticated attacker can exploit to delete arbitrary files and even execute malicious code "under certain circumstances."
The vulnerability is due to unsafe usage of PHP's unserialize() on user-supplied input, which allows an unauthenticated hacker to delete arbitrary files and possibly execute arbitrary code on a vBulletin installation.
A publicly exposed API, called vB_Library_Template's cacheTemplates() function, allows fetching information on a set of given templates from the database to store them inside a cache variable.
"$temnplateidlist variable, which can come directly from user-input, is directly supplied to unserialize(), resulting in an arbitrary deserialization primitive," the advisory explains.Besides technical details, the advisory also includes Proof-of-Concept (PoC) exploit code to explain the severity of this vulnerability.
We expect the vendor to release the patch for both the security flaws before hackers started exploiting them to target vBulletin installations.
Have something to say about this article? Comment below or share it with us on Facebook, Twitter or our LinkedIn Group.