Security researchers have publicly disclosed an unpatched zero-day vulnerability in the firmware of AT&T DirecTV WVB kit after trying to get the device manufacturer to patch this easy-to-exploit flaw over the past few months.
The problem is with a core component of the Genie DVR system that's shipped free of cost with DirecTV and can be easily exploited by hackers to gain root access and take full control of the device, placing millions of people who've signed up to DirecTV service at risk.
The vulnerability actually resides in WVBR0-25—a Linux-powered wireless video bridge manufactured by Linksys that AT&T provides to its new customers.
DirecTV Wireless Video Bridge WVBR0-25 allows the main Genie DVR to communicate over the air with customers' Genie client boxes (up to 8) that are plugged into their TVs around the home.
Trend Micro researcher Ricky Lawshae, who is also a DirecTV customer, decided to take a closer look at the device and found that Linksys WVBR0-25 hands out internal diagnostic information from the device's web server, without requiring any authentication.
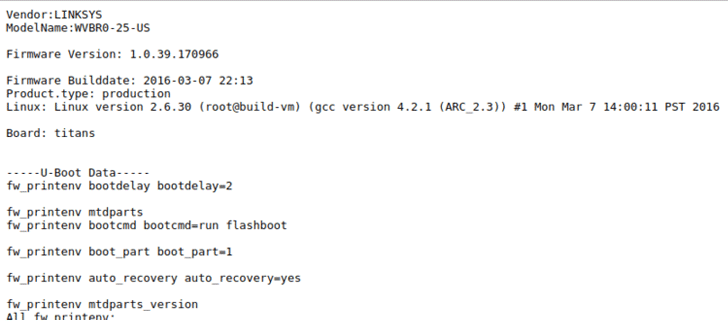
When trying to browse to the wireless bridge's web server on the device, Lawshae was expecting a login page or similar, but instead, he found "a wall of text streaming before [his] eyes."
Once there, Lawshae was able to see the output of several diagnostic scripts containing everything about the DirecTV Wireless Video Bridge, including the WPS pin, connected clients, running processes, and much more.
What's more worrisome was that the device was accepting his commands remotely and that too at the "root" level, meaning Lawshae could have run software, exfiltrate data, encrypt files, and do almost anything he wanted on the Linksys device.
The vulnerability was reported by the ZDI Initiative to Linksys more than six months ago, but the vendor ceased communication with the researcher and had yet not fixed the problem, leaving this easy-to-exploit vulnerability unpatched and open for hackers.
So, after over half a year, ZDI decided to publicize the zero-day vulnerability, and recommended users to limit their devices that can interact with Linksys WVBR0-25 "to those that actually need to reach" in order to protect themselves.
The problem is with a core component of the Genie DVR system that's shipped free of cost with DirecTV and can be easily exploited by hackers to gain root access and take full control of the device, placing millions of people who've signed up to DirecTV service at risk.
The vulnerability actually resides in WVBR0-25—a Linux-powered wireless video bridge manufactured by Linksys that AT&T provides to its new customers.
DirecTV Wireless Video Bridge WVBR0-25 allows the main Genie DVR to communicate over the air with customers' Genie client boxes (up to 8) that are plugged into their TVs around the home.
Trend Micro researcher Ricky Lawshae, who is also a DirecTV customer, decided to take a closer look at the device and found that Linksys WVBR0-25 hands out internal diagnostic information from the device's web server, without requiring any authentication.
When trying to browse to the wireless bridge's web server on the device, Lawshae was expecting a login page or similar, but instead, he found "a wall of text streaming before [his] eyes."
Once there, Lawshae was able to see the output of several diagnostic scripts containing everything about the DirecTV Wireless Video Bridge, including the WPS pin, connected clients, running processes, and much more.
What's more worrisome was that the device was accepting his commands remotely and that too at the "root" level, meaning Lawshae could have run software, exfiltrate data, encrypt files, and do almost anything he wanted on the Linksys device.
"It literally took 30 seconds of looking at this device to find and verify an unauthenticated, remote root command injection vulnerability. It was at this point that I became pretty frustrated," Lawshae wrote in an advisory published Wednesday on Trend Micro-owned Zero Day Initiative (ZDI) website.
"The vendors involved here should have had some form of secure development to prevent bugs like this from shipping. More than that, we as security practitioners have failed to affect the changes needed in the industry to prevent these simple yet impactful bugs from reaching unsuspecting consumers."Lawshae also provided a video, demonstrating how a quick and straightforward hack let anyone get a root shell on the DirecTV wireless box in less than 30 seconds, granting them full remote unauthenticated admin control over the device.
So, after over half a year, ZDI decided to publicize the zero-day vulnerability, and recommended users to limit their devices that can interact with Linksys WVBR0-25 "to those that actually need to reach" in order to protect themselves.
Have something to say about this article? Comment below or share it with us on Facebook, Twitter or our LinkedIn Group.