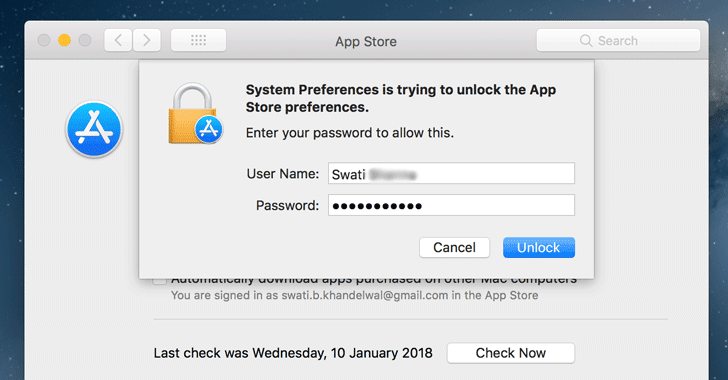
Yet another password vulnerability has been uncovered in macOS High Sierra, which unlocks App Store System Preferences with any password (or no password at all).
A new password bug has been discovered in the latest version of macOS High Sierra that allows anyone with access to your Mac to unlock App Store menu in System Preferences with any random password or no password at all.
The impact of this vulnerability is nowhere as serious as the previously disclosed root login bug in Apple's desktop OS that enabled access to the root superuser account simply by entering a blank password on macOS High Sierra 10.13.1.
As reported on Open Radar earlier this week, the vulnerability impacts macOS version 10.13.2 and requires the attacker to be logged in with an administrator-level account for this vulnerability to work.
I checked the bug on my fully updated Mac laptop, and it worked by entering a blank password as well as any random password.
If you're running latest macOS High Sierra, check yourself:
Once done, you'll gain full access to App Store settings, allowing you to modify settings like disabling automatic installation of macOS updates, app updates, system data files and even security updates that would patch vulnerabilities.
We also tried to reproduce the same bug on the latest developer beta 4 of macOS High Sierra 10.13.3, but it did not work, suggesting Apple probably already knows about this issue and you'll likely get a fix in this upcoming software update.
What's wrong with password prompts in macOS? It's high time Apple should stop shipping updates with such an embarrassing bug.
Apple also patched a similar vulnerability in October in macOS, which affected encrypted volumes using APFS wherein the password hint section was showing the actual password of the user in the plain text.
A new password bug has been discovered in the latest version of macOS High Sierra that allows anyone with access to your Mac to unlock App Store menu in System Preferences with any random password or no password at all.
The impact of this vulnerability is nowhere as serious as the previously disclosed root login bug in Apple's desktop OS that enabled access to the root superuser account simply by entering a blank password on macOS High Sierra 10.13.1.
As reported on Open Radar earlier this week, the vulnerability impacts macOS version 10.13.2 and requires the attacker to be logged in with an administrator-level account for this vulnerability to work.
I checked the bug on my fully updated Mac laptop, and it worked by entering a blank password as well as any random password.
If you're running latest macOS High Sierra, check yourself:
- Log in as a local administrator
- Go to System Preferences and then App Store
- Click on the padlock icon (double-click on the lock if it is already unlocked)
- Enter any random password (or leave it blank) in login window
- Click Unlock, Ta-da!
Once done, you'll gain full access to App Store settings, allowing you to modify settings like disabling automatic installation of macOS updates, app updates, system data files and even security updates that would patch vulnerabilities.
We also tried to reproduce the same bug on the latest developer beta 4 of macOS High Sierra 10.13.3, but it did not work, suggesting Apple probably already knows about this issue and you'll likely get a fix in this upcoming software update.
What's wrong with password prompts in macOS? It's high time Apple should stop shipping updates with such an embarrassing bug.
Apple also patched a similar vulnerability in October in macOS, which affected encrypted volumes using APFS wherein the password hint section was showing the actual password of the user in the plain text.
Have something to say about this article? Comment below or share it with us on Facebook, Twitter or our LinkedIn Group.