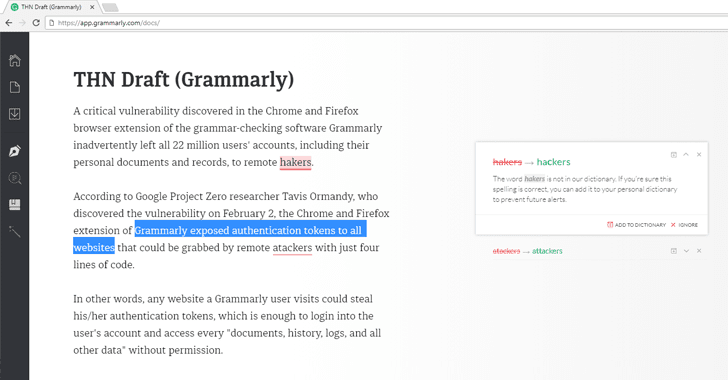
A critical vulnerability discovered in the Chrome and Firefox browser extension of the grammar-checking software Grammarly inadvertently left all 22 million users' accounts, including their personal documents and records, vulnerable to remote hackers.
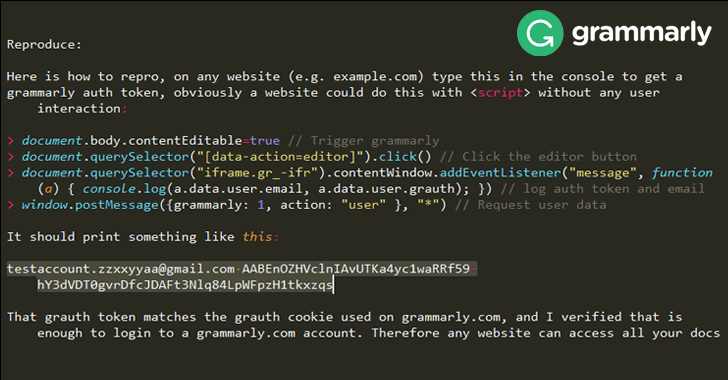
According to Google Project Zero researcher Tavis Ormandy, who discovered the vulnerability on February 2, the Chrome and Firefox extension of Grammarly exposed authentication tokens to all websites that could be grabbed by remote attackers with just 4 lines of JavaScript code.
In other words, any website a Grammarly user visits could steal his/her authentication tokens, which is enough to login into the user's account and access every "documents, history, logs, and all other data" without permission.
"I'm calling this a high severity bug, because it seems like a pretty severe violation of user expectations," Ormandy said in a vulnerability report. "Users would not expect that visiting a website gives it permission to access documents or data they've typed into other websites."Ormandy has also provided a proof-of-concept (PoC) exploit, which explains how one can easily trigger this serious bug to steal Grammarly user's access token with just four lines of code.
This high-severity flaw was discovered on Friday and fixed early Monday morning by the Grammarly team, which, according to the researcher, is "a really impressive response time" for addressing such bugs.
Security updates are now available for both Chrome and Firefox browser extensions, which should get automatically updated without requiring any action by Grammarly users.
A Grammarly spokesperson also told in an email that the company has no evidence of users being compromised by this vulnerability.
"Grammarly resolved a security bug reported by Google's Project Zero security researcher, Tavis Ormandy, within hours of its discovery. At this time, Grammarly has no evidence that any user information was compromised by this issue," the spokesperson said.
"We're continuing to monitor actively for any unusual activity. The security issue potentially affected text saved in the Grammarly Editor. This bug did not affect the Grammarly Keyboard, the Grammarly Microsoft Office add-in, or any text typed on websites while using the Grammarly browser extension. The bug is fixed, and there is no action required by Grammarly users."Stay tuned for more updates.
Have something to say about this article? Comment below or share it with us on Facebook, Twitter or our LinkedIn Group.