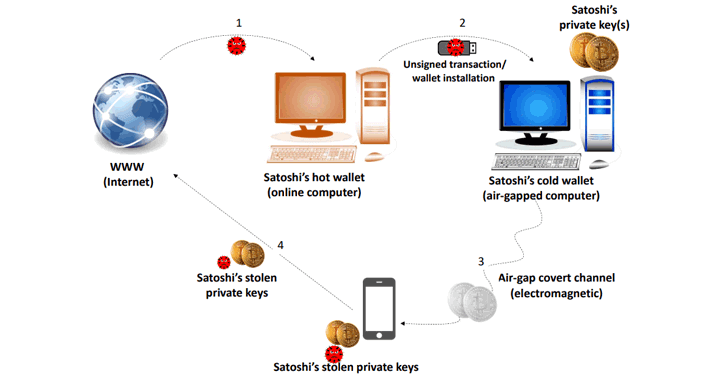
Dr. Mordechai Guri, the head of R&D team at Israel's Ben Gurion University, who previously demonstrated various methods to steal data from an air-gapped computer, has now published new research named "BeatCoin."
BeatCoin is not a new hacking technique; instead, it's an experiment wherein the researcher demonstrates how all previously discovered out-of-band communication methods can be used to steal private keys for a cryptocurrency wallet installed on cold storage, preferably an air-gapped computer or Raspberry Pi.
For those unaware, keeping your cryptocurrency protected in a wallet on a device which is entirely offline is called cold storage. Since online digital wallets carry different security risks, some people prefer keeping their private keys offline.
Air-gapped computers are those that are isolated from the Internet, local networks, Bluetooth and therefore, are believed to be the most secure devices and are difficult to infiltrate or exfiltrate.
If you are new to this topic, we recommend reading our previous articles, detailing how highly-motivated attackers can use specially designed malware to exfiltrate data from an air-gapped computer via light, sound, heat, electromagnetic, magnetic, infrared, and ultrasonic waves.
For BeatCoin experiment, Dr. Guri deployed malware on an air-gapped computer that runs a Bitcoin wallet application and then performed each attack vector one-by-one to transmit the wallet keys to a nearby device over covert channels.
Guri has also shared two videos. The first one demonstrates exfiltration of private keys from an air-gapped computer, which hardly took a few seconds to transmit data to a nearby smartphone using ultrasonic waves.
In the second video, the researcher transmitted private keys stored on a Raspberry Pi device to the nearby smartphone using the RadIoT attack—a technique to exfiltrate data from air-gapped internet-of-things (IoT) and embedded devices via radio signals.
BeatCoin is not a new hacking technique; instead, it's an experiment wherein the researcher demonstrates how all previously discovered out-of-band communication methods can be used to steal private keys for a cryptocurrency wallet installed on cold storage, preferably an air-gapped computer or Raspberry Pi.
For those unaware, keeping your cryptocurrency protected in a wallet on a device which is entirely offline is called cold storage. Since online digital wallets carry different security risks, some people prefer keeping their private keys offline.
Air-gapped computers are those that are isolated from the Internet, local networks, Bluetooth and therefore, are believed to be the most secure devices and are difficult to infiltrate or exfiltrate.
If you are new to this topic, we recommend reading our previous articles, detailing how highly-motivated attackers can use specially designed malware to exfiltrate data from an air-gapped computer via light, sound, heat, electromagnetic, magnetic, infrared, and ultrasonic waves.
For BeatCoin experiment, Dr. Guri deployed malware on an air-gapped computer that runs a Bitcoin wallet application and then performed each attack vector one-by-one to transmit the wallet keys to a nearby device over covert channels.
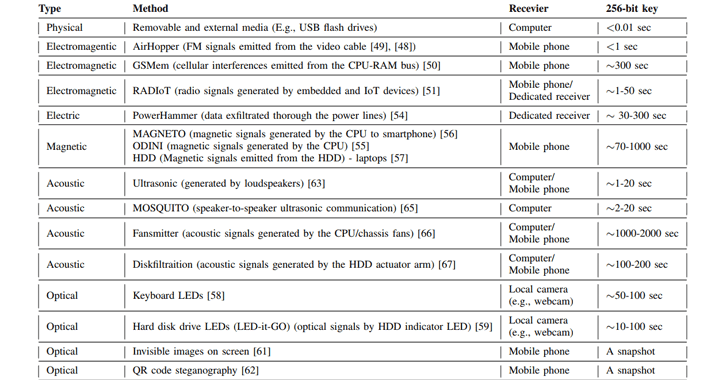
"In the adversarial attack model, the attacker infiltrates the offline wallet, infecting it with malicious code," the paper [PDF] reads. "The malware can be pre-installed or pushed in during the initial installation of the wallet, or it can infect the system when removable media (e.g., USB flash drive) is inserted into the wallet's computer in order to sign a transaction. These attack vectors have repeatedly been proven feasible in the last decade."Results shown in the above chart suggests AirHopper, MOSQUITO, and Ultrasonic techniques are the fastest way to transmit a 256-bit private key to a remote receiver, whereas, Diskfiltration and Fansmitter methods take minutes.
Guri has also shared two videos. The first one demonstrates exfiltration of private keys from an air-gapped computer, which hardly took a few seconds to transmit data to a nearby smartphone using ultrasonic waves.
"The radio signals - generated from various buses and general-purpose input/output (GPIO) pins of the embedded devices - can be modulated with binary data. In this case, the transmissions can be received by an AM or FM receiver located nearby the device."In the last research published earlier this month, Guri's team also demonstrated how hackers could use power fluctuations in the current flow "propagated through the power lines" to covertly exfiltrate highly sensitive data out of an air gapped-computer.
Have something to say about this article? Comment below or share it with us on Facebook, Twitter or our LinkedIn Group.