Security researchers are warning of almost a decade old issue with one of the Apple's macOS feature which was designed for users' convenience but is potentially exposing the contents of files stored on password-protected encrypted drives.
Earlier this month, security researcher Wojciech Regula from SecuRing published a blog post, about the "Quick Look" feature in macOS that helps users preview photos, documents files, or a folder without opening them.
Regula explained that Quick Look feature generates thumbnails for each file/folder, giving users a convenient way to evaluate files before they open them.
However, these cached thumbnails are stored on the computer's non-encrypted hard drive, at a known and unprotected location, even if those files/folders belong to an encrypted container, eventually revealing some of the content stored on encrypted drives.
Patrick Wardle, chief research officer at Digital Security, equally shared the concern, saying that the issue has long been known for at least eight years, "however the fact that behavior is still present in the latest version of macOS, and (though potentially having serious privacy implications), is not widely known by Mac users, warrants additional discussion."
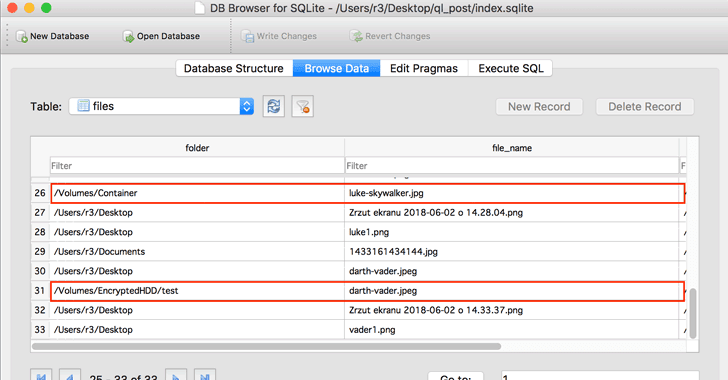
To prove his claim, Regula created two new encrypted containers, one using VeraCrypt software and the second with macOS Encrypted HFS+/APFS drives, and then saved a photo in each of them.
As explained in his post, after running a simple command on his system, Regula was able to find the path and cached files for both images left outside the encrypted containers.
"It means that all photos that you have previewed using space (or Quicklook cached them independently) are stored in that directory as a miniature and its path," Regula said.
In a separate blog post, Wardle demonstrated that macOS behaves same for the password-protected encrypted AFPS containers, eventually exposing even encrypted volumes to potential snooping.
Wardle also noted that if you connect a USB drive with your Mac computer, the system will create thumbnails of files residing on the external drive and store them on its boot drive.
Wardle believes it would be pretty easy for Apple to resolve this issue by either not generating a preview if the file is within an encrypted container, or deleting the cache when a volume is unmounted.
Until and unless Apple resolves this issue in future, Wardles advises users to manually delete the QuickLook cache when they unmount an encrypted container.
Earlier this month, security researcher Wojciech Regula from SecuRing published a blog post, about the "Quick Look" feature in macOS that helps users preview photos, documents files, or a folder without opening them.
Regula explained that Quick Look feature generates thumbnails for each file/folder, giving users a convenient way to evaluate files before they open them.
However, these cached thumbnails are stored on the computer's non-encrypted hard drive, at a known and unprotected location, even if those files/folders belong to an encrypted container, eventually revealing some of the content stored on encrypted drives.
Patrick Wardle, chief research officer at Digital Security, equally shared the concern, saying that the issue has long been known for at least eight years, "however the fact that behavior is still present in the latest version of macOS, and (though potentially having serious privacy implications), is not widely known by Mac users, warrants additional discussion."
To prove his claim, Regula created two new encrypted containers, one using VeraCrypt software and the second with macOS Encrypted HFS+/APFS drives, and then saved a photo in each of them.
As explained in his post, after running a simple command on his system, Regula was able to find the path and cached files for both images left outside the encrypted containers.
"It means that all photos that you have previewed using space (or Quicklook cached them independently) are stored in that directory as a miniature and its path," Regula said.
In a separate blog post, Wardle demonstrated that macOS behaves same for the password-protected encrypted AFPS containers, eventually exposing even encrypted volumes to potential snooping.
"If we unmount the encrypted volume, the thumbnails of the file are (as previously mentioned) still stored in the user's temporary directory, and thus can be extracted," Wardle said.
"If an attacker (or law enforcement) has access to the running system, even if the password-protected encrypted containers are unmounted (as thus their contents 'safe'), this caching 'feature' can reveal their contents."
Wardle also noted that if you connect a USB drive with your Mac computer, the system will create thumbnails of files residing on the external drive and store them on its boot drive.
Wardle believes it would be pretty easy for Apple to resolve this issue by either not generating a preview if the file is within an encrypted container, or deleting the cache when a volume is unmounted.
Until and unless Apple resolves this issue in future, Wardles advises users to manually delete the QuickLook cache when they unmount an encrypted container.
Have something to say about this article? Comment below or share it with us on Facebook, Twitter or our LinkedIn Group.