As it was speculated that the author of LuminosityLink RAT was arrested last year, a plea agreement made available to the public today confirmed the news.
Back in September last year, Europol's European Cybercrime Centre (EC3) and National Crime Agency began the crackdown on the LuminosityLink RAT, targeting sellers and users of the malware, which resulted in the seizure of a considerable number of computers and internet accounts across the world, and complete takedown of the threat.
Colton Grubbs, a 21-year-old man from Kentucky, the developer of the LumunosityLink RAT has pleaded guilty to federal charges of creating, selling and providing technical support for the malware to his customers, who used it to gain unauthorized access to thousands of computers across 78 countries worldwide.
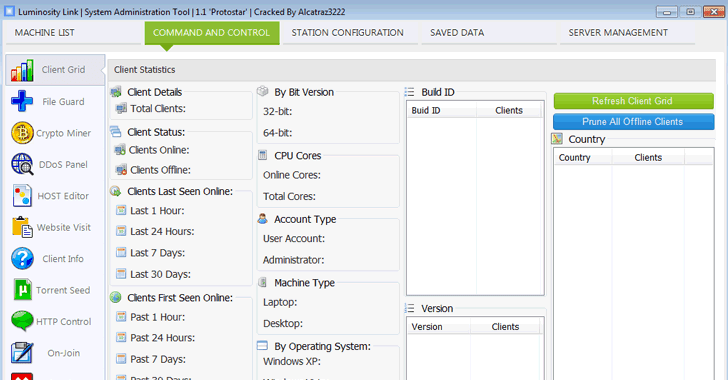
First surfaced in April 2015, the LuminosityLink RAT (Remote Access Trojan), also known as Luminosity, was a hacking tool that was sold for $40, marketing itself as a legitimate tool for Windows administrators to "manage a large amount of computers concurrently."
However, in reality, LuminosityLink was a dangerous remote access trojan designed to disable anti-virus and anti-malware protection installed on a victim's computer in order remain undetected, and then began its other nefarious activities, which included:
Grubbs, who was using online moniker of 'KFC Watermelon,' marketed and sold LuminosityLink on his luminosity.link website and public internet forum HackForums.net. The malware was sold to more than 6,000 individuals, who used it maliciously to take over tens of thousands of computers in 78 countries.
Previously Grubbs claimed that LuminosityLink was legitimate software for system admins, but in Monday's plea agreement, the author admitted that he knew some of its customers were using it to illegally hack into victims' computers without their knowledge or permission.
Three days later, Grubbs also transferred more than 114 bitcoin (around $273,000 at the time) from his LuminosityLink bitcoin address to six new bitcoin addresses.
Grubbs has now pleaded guilty to 3 counts of invasion of privacy, conspiracy, and causing loss of at least $5,000 to the protected computers, which carry punishments of up to 25 years in prison and fines of $750,000.
Back in September last year, Europol's European Cybercrime Centre (EC3) and National Crime Agency began the crackdown on the LuminosityLink RAT, targeting sellers and users of the malware, which resulted in the seizure of a considerable number of computers and internet accounts across the world, and complete takedown of the threat.
Colton Grubbs, a 21-year-old man from Kentucky, the developer of the LumunosityLink RAT has pleaded guilty to federal charges of creating, selling and providing technical support for the malware to his customers, who used it to gain unauthorized access to thousands of computers across 78 countries worldwide.
First surfaced in April 2015, the LuminosityLink RAT (Remote Access Trojan), also known as Luminosity, was a hacking tool that was sold for $40, marketing itself as a legitimate tool for Windows administrators to "manage a large amount of computers concurrently."
However, in reality, LuminosityLink was a dangerous remote access trojan designed to disable anti-virus and anti-malware protection installed on a victim's computer in order remain undetected, and then began its other nefarious activities, which included:
- activating the webcam on the victim's computer to spying on video feeds,
- accessing and viewing documents, photographs, and other files,
- recovering passwords,
- injecting an aggressive keylogger in almost every running process on the infected computer to automatically record all the keystrokes entered by the victim.
Grubbs, who was using online moniker of 'KFC Watermelon,' marketed and sold LuminosityLink on his luminosity.link website and public internet forum HackForums.net. The malware was sold to more than 6,000 individuals, who used it maliciously to take over tens of thousands of computers in 78 countries.
Previously Grubbs claimed that LuminosityLink was legitimate software for system admins, but in Monday's plea agreement, the author admitted that he knew some of its customers were using it to illegally hack into victims' computers without their knowledge or permission.
"Defendant's marketing emphasized these malicious features of LuminosityLink, including that it could be remotely installed without notification, record the keys that a victim pressed on their keyboard, surveil victims using their computer cameras and microphones, view and download the computer's files, steal names and passwords used to access websites, mine and earn virtual currency using victim computers and electricity, use victim computers to launch DDoS attacks against other computers, and prevent anti-malware software from detecting and removing LuminosityLink," the plea agreement signed by Grubbs reads.Grubbs also admitted that when he learned of an FBI raid on his apartment in July last year, he tried to hide evidence—including his laptop, hard drives, a debit card associated with his bitcoin account and a phone storing his bitcoin information—before the authorized search.
Three days later, Grubbs also transferred more than 114 bitcoin (around $273,000 at the time) from his LuminosityLink bitcoin address to six new bitcoin addresses.
Grubbs has now pleaded guilty to 3 counts of invasion of privacy, conspiracy, and causing loss of at least $5,000 to the protected computers, which carry punishments of up to 25 years in prison and fines of $750,000.
Have something to say about this article? Comment below or share it with us on Facebook, Twitter or our LinkedIn Group.