Almost three years after the arrest of two young Dutch brothers, who pleaded guilty to their involvement in creating and distributing CoinVault ransomware malware, a district court in Rotterdam today sentenced them to 240 hours of community service.
In 2015, the two suspects — Melvin (25-year-old) and Dennis van den B. (21-year-old) — were arrested from Amersfoort on suspicion of involvement in CoinVault ransomware attacks.
The duo was arrested by law enforcement with the help of researchers from Kaspersky Labs, who reverse-engineered the malware and found the full name of one of the suspects and their IP address left accidentally on the command and control server.
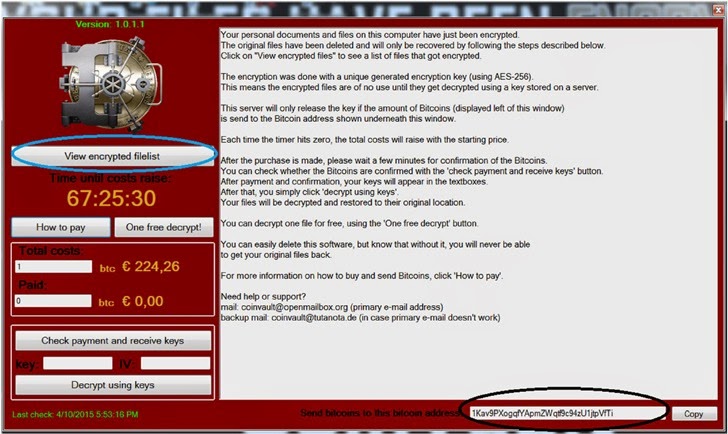
CoinVault ransomware campaign that began in May 2014 was one of the most successful file-encrypting ransomware program of its time that encrypted over 14,000 Windows computers worldwide, primarily the Netherlands, the US, the UK, Germany, and France.
Just like other ransomware attacks, the sole intent of CoinVault was also extorting money from victims, and the suspects successfully managed to extract money out of almost 1,300 people.
Since the duo fully cooperated in the police investigation and have a clean criminal record, the court decided to punish them only with 240 hours of community service, which is the maximum term of community service someone can serve.
Besides community service time, the court has also ordered the suspects to pay compensation to some of their victims.
In 2015, following the duo's arrest and the seizure of the command and control server, Kaspersky released a ransomware decryption tool for Coinvault victims, allowing them to unlock their locked file for free.
Also Read: This Ransomware Malware Could Poison Your Water Supply If Not Paid
Since CoinVault, we have seen some major ransomware outbreaks, including WannaCry and NotPetya, which wreaked global havoc by infecting thousands of businesses and millions of customers across the world.
The best way to prevent yourself from being a victim of such ransomware attacks in the first place is never to open suspicious files and links provided in an email.
And most importantly, always keep a good backup routine and updated antivirus software in place.
In 2015, the two suspects — Melvin (25-year-old) and Dennis van den B. (21-year-old) — were arrested from Amersfoort on suspicion of involvement in CoinVault ransomware attacks.
The duo was arrested by law enforcement with the help of researchers from Kaspersky Labs, who reverse-engineered the malware and found the full name of one of the suspects and their IP address left accidentally on the command and control server.
CoinVault ransomware campaign that began in May 2014 was one of the most successful file-encrypting ransomware program of its time that encrypted over 14,000 Windows computers worldwide, primarily the Netherlands, the US, the UK, Germany, and France.
Just like other ransomware attacks, the sole intent of CoinVault was also extorting money from victims, and the suspects successfully managed to extract money out of almost 1,300 people.
Since the duo fully cooperated in the police investigation and have a clean criminal record, the court decided to punish them only with 240 hours of community service, which is the maximum term of community service someone can serve.
Besides community service time, the court has also ordered the suspects to pay compensation to some of their victims.
In 2015, following the duo's arrest and the seizure of the command and control server, Kaspersky released a ransomware decryption tool for Coinvault victims, allowing them to unlock their locked file for free.
Also Read: This Ransomware Malware Could Poison Your Water Supply If Not Paid
Since CoinVault, we have seen some major ransomware outbreaks, including WannaCry and NotPetya, which wreaked global havoc by infecting thousands of businesses and millions of customers across the world.
The best way to prevent yourself from being a victim of such ransomware attacks in the first place is never to open suspicious files and links provided in an email.
And most importantly, always keep a good backup routine and updated antivirus software in place.
Have something to say about this article? Comment below or share it with us on Facebook, Twitter or our LinkedIn Group.