WhatsApp, the most popular messaging application in the world, has been found vulnerable to multiple security vulnerabilities that could allow malicious users to intercept and modify the content of messages sent in both private as well as group conversations.
Discovered by security researchers at Israeli security firm Check Point, the flaws take advantage of a loophole in WhatsApp's security protocols to change the content of the messages, allowing malicious users to create and spread misinformation or fake news from "what appear to be trusted sources."
The flaws reside in the way WhatsApp mobile application connects with the WhatsApp Web and decrypts end-to-end encrypted messages using the protobuf2 protocol.
The vulnerabilities could allow hackers to misuse the 'quote' feature in a WhatsApp group conversation to change the identity of the sender, or alter the content of someone else's reply to a group chat, or even send private messages to one of the group participants (but invisible to other members) disguised as a group message for all.
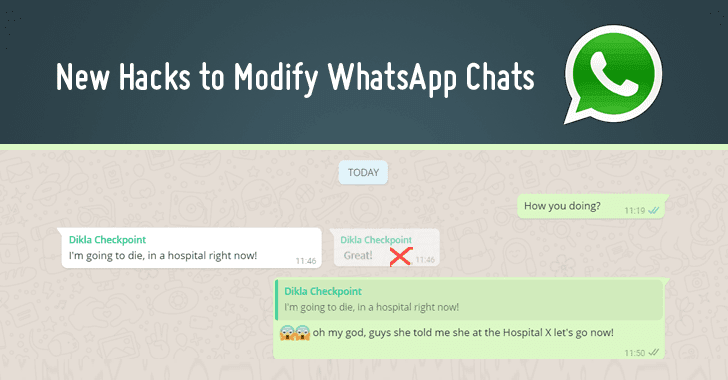
In an example, the researchers were able to change a WhatsApp chat entry that said "Great!"—sent by one member of a group—to read "I'm going to die, in a hospital right now!"
It should be noted that the reported vulnerabilities do not allow a third person to intercept or modify end-to-end encrypted WhatsApp messages, but instead, the flaws could be exploited only by malicious users who are already part of group conversations.
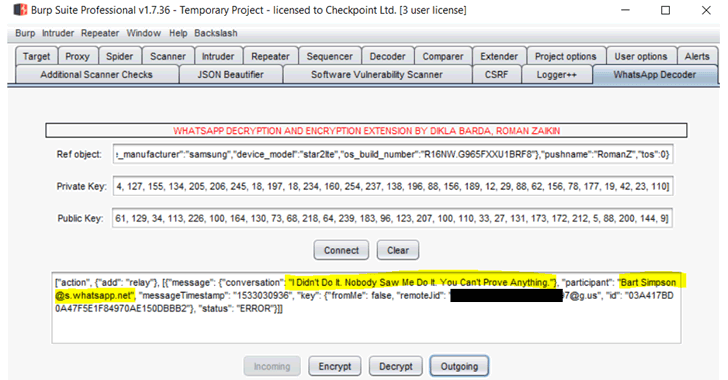
To exploit these vulnerabilities, the CheckPoint researchers—Dikla Barda, Roman Zaikin, and Oded Vanunu—created a new custom extension for the popular web application security software Burp Suite, allowing them to easily intercept and modify sent and received encrypted messages on their WhatsApp Web.
The tool, which they named "WhatsApp Protocol Decryption Burp Tool," is available for free on Github, and first requires an attacker to input its private and public keys, which can be obtained easily "obtained from the key generation phase from WhatsApp Web before the QR code is generated," as explained by the trio in a blog post.
Using the Burp Suite extension, a malicious WhatsApp user can alter the content of someone else's reply, essentially putting words in their mouth, as shown in the video.
The third WhatsApp attack allows a malicious group user to send a specially crafted message that only a specific person will be able to see. If the targeted individual responds to the same message, only then its content will get displayed to everyone in the group.
The trio reported the flaws to the WhatsApp security team, but the company argued that since these messages do not break the fundamental functionality of the end-to-end encryption, users "always have the option of blocking a sender who tries to spoof messages and they can report problematic content to us."
Discovered by security researchers at Israeli security firm Check Point, the flaws take advantage of a loophole in WhatsApp's security protocols to change the content of the messages, allowing malicious users to create and spread misinformation or fake news from "what appear to be trusted sources."
The flaws reside in the way WhatsApp mobile application connects with the WhatsApp Web and decrypts end-to-end encrypted messages using the protobuf2 protocol.
The vulnerabilities could allow hackers to misuse the 'quote' feature in a WhatsApp group conversation to change the identity of the sender, or alter the content of someone else's reply to a group chat, or even send private messages to one of the group participants (but invisible to other members) disguised as a group message for all.
In an example, the researchers were able to change a WhatsApp chat entry that said "Great!"—sent by one member of a group—to read "I'm going to die, in a hospital right now!"
It should be noted that the reported vulnerabilities do not allow a third person to intercept or modify end-to-end encrypted WhatsApp messages, but instead, the flaws could be exploited only by malicious users who are already part of group conversations.
Video Demonstration — How to Modify WhatsApp Chats
The tool, which they named "WhatsApp Protocol Decryption Burp Tool," is available for free on Github, and first requires an attacker to input its private and public keys, which can be obtained easily "obtained from the key generation phase from WhatsApp Web before the QR code is generated," as explained by the trio in a blog post.
"By decrypting the WhatsApp communication, we were able to see all the parameters that are actually sent between the mobile version of WhatsApp and the Web version. This allowed us to then be able to manipulate them and start looking for security issues."In the above-shown YouTube video, researchers demonstrated the three different techniques they have developed, which allowed them to:
Attack 1 — Changing a Correspondent's Reply To Put Words in Their Mouth
Using the Burp Suite extension, a malicious WhatsApp user can alter the content of someone else's reply, essentially putting words in their mouth, as shown in the video.
Attack 2 — Change the Identity of a Sender in a Group Chat, Even If They Are Not a Member
The attack allows a malicious user in a WhatsApp group to exploit the 'quote' feature—that lets users reply to a past message within a chat by tagging it—in a conversation to spoof a reply message to impersonate another group member and even a non-existing group member.Attack 3 — Send a Private Message in a Chat Group But When The Recipient Replies, The Whole Group Sees It
The third WhatsApp attack allows a malicious group user to send a specially crafted message that only a specific person will be able to see. If the targeted individual responds to the same message, only then its content will get displayed to everyone in the group.
WhatsApp/Facebook Choose to Left Reported Attacks Unpatched
The trio reported the flaws to the WhatsApp security team, but the company argued that since these messages do not break the fundamental functionality of the end-to-end encryption, users "always have the option of blocking a sender who tries to spoof messages and they can report problematic content to us."
"These are known design trade-offs that have been previously raised in public, including by Signal in a 2014 blog post, and we do not intend to make any change to WhatsApp at this time," WhatsApp security team replied to the researchers.Another argument WhatsApp shared with researchers, in context of why the company can not stop the modification of the message content—"This is a known edge case that relates to the fact that we do not store messages on our servers and do not have a single source of truth for these messages."
"My point was the misinformation, and WhatsApp plays a vital role in our day activity. So, In my point of view they indeed have to fix these issues," CheckPoint researcher Roman Zaikin said.Since WhatsApp has become one of the biggest tools to spread fake news and misinformation, at least in countries with highly volatile political issues, we believe WhatsApp should fix these problems along with putting limits on the forwarded messages.
"It's always functionality vs. security, and this time WhatsApp choose functionality."
Have something to say about this article? Comment below or share it with us on Facebook, Twitter or our LinkedIn Group.