Cybersecurity researchers have revealed an unpatched logical flaw in Microsoft Office 2016 and older versions that could allow an attacker to embed malicious code inside a document file, tricking users into running malware onto their computers.
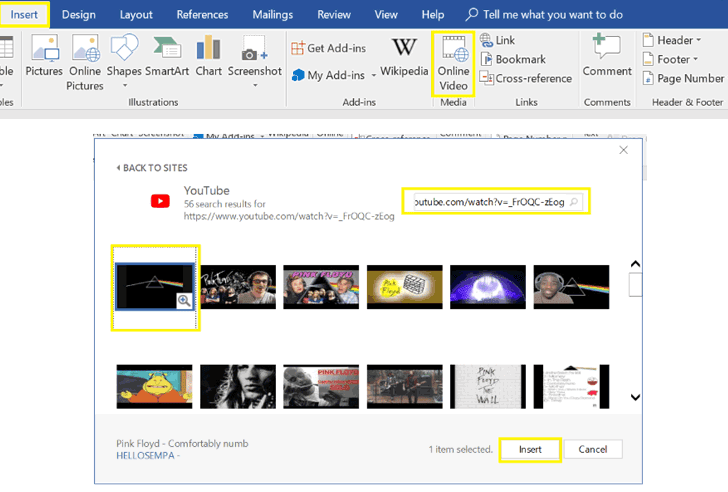
Discovered by researchers at Cymulate, the bug abuses the 'Online Video' option in Word documents, a feature that allows users to embedded an online video with a link to YouTube, as shown.
When a user adds an online video link to an MS Word document, the Online Video feature automatically generates an HTML embed script, which is executed when the thumbnail inside the document is clicked by the viewer.
Researchers decided to go public with their findings three months after Microsoft refused to acknowledge the reported issue as a security vulnerability.
Since the Word Doc files (.docx) are actually zip packages of its media and configuration files, it can easily be opened and edited.
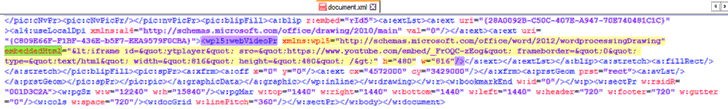
According to the researchers, the configuration file called 'document.xml,' which is a default XML file used by Word and contains the generated embedded-video code, can be edited to replace the current video iFrame code with any HTML or javascript code that would run in the background.
In simple words, an attacker can exploit the bug by replacing the actual YouTube video with a malicious one that would get executed by the Internet Explorer Download Manager.
To prove the extent of the vulnerability, Cymulate researchers created a proof-of-concept attack, demonstrating how a maliciously crafted document with an embed video, which if clicked, would prompt user to run an embedded executable (as a blob of a base64)–without downloading anything from the internet or displaying any security warning when the victim clicks on the video thumbnail.
The hack requires an attacker to convince victims into opening a document and then clicking on an embedded video link.
Cymulate researchers responsibly reported this bug, which impacts all users with MS Office 2016 and older versions of the productivity suite, three months ago to Microsoft, but the company refused to acknowledge it as a security vulnerability.
Apparently, Microsoft has no plans to fix the issue and says its software is "properly interpreting HTML as designed."
Meanwhile, researchers recommended enterprise administrators to block Word documents containing the embedded video tag: "embeddedHtml" in the Document.xml file, and end users are advised not to open uninvited email attachments from unknown or suspicious sources.
Discovered by researchers at Cymulate, the bug abuses the 'Online Video' option in Word documents, a feature that allows users to embedded an online video with a link to YouTube, as shown.
When a user adds an online video link to an MS Word document, the Online Video feature automatically generates an HTML embed script, which is executed when the thumbnail inside the document is clicked by the viewer.
Researchers decided to go public with their findings three months after Microsoft refused to acknowledge the reported issue as a security vulnerability.
How Does the New MS Word Attack Works?
Since the Word Doc files (.docx) are actually zip packages of its media and configuration files, it can easily be opened and edited.
According to the researchers, the configuration file called 'document.xml,' which is a default XML file used by Word and contains the generated embedded-video code, can be edited to replace the current video iFrame code with any HTML or javascript code that would run in the background.
In simple words, an attacker can exploit the bug by replacing the actual YouTube video with a malicious one that would get executed by the Internet Explorer Download Manager.
"Inside the .xml file, look for the embeddedHtml parameter (under WebVideoPr) which contains the Youtube iframe code," the researchers said. "Save the changes in the document.xml file, update the docx package with the modified XML and open the document. No security warning is presented while opening this document with Microsoft Word."
Video Demonstration: MS Word Online Video Flaw
To prove the extent of the vulnerability, Cymulate researchers created a proof-of-concept attack, demonstrating how a maliciously crafted document with an embed video, which if clicked, would prompt user to run an embedded executable (as a blob of a base64)–without downloading anything from the internet or displaying any security warning when the victim clicks on the video thumbnail.
The hack requires an attacker to convince victims into opening a document and then clicking on an embedded video link.
Cymulate researchers responsibly reported this bug, which impacts all users with MS Office 2016 and older versions of the productivity suite, three months ago to Microsoft, but the company refused to acknowledge it as a security vulnerability.
Apparently, Microsoft has no plans to fix the issue and says its software is "properly interpreting HTML as designed."
Meanwhile, researchers recommended enterprise administrators to block Word documents containing the embedded video tag: "embeddedHtml" in the Document.xml file, and end users are advised not to open uninvited email attachments from unknown or suspicious sources.
Have something to say about this article? Comment below or share it with us on Facebook, Twitter or our LinkedIn Group.