Cybersecurity experts all echo the same thing – cyber attacks are going to get more rampant, and they will continue to pose severe threats against all technology users.
Businesses, in particular, have become prime targets for cybercriminals due to the nature of data and information they process and store.
2018 saw a slew of data breaches targeting large enterprises that resulted in the theft of the personal and financial records of millions of customers.
Falling victim to cyber attacks can deal with a major financial blow to businesses as the cost of dealing with an attack has risen to $1.1 million on the average. It can even be more devastating for small to medium-sized businesses.
60 percent of these smaller operations close within six months after failing to recover from cyber attacks. But aside from these monetary costs, companies can also lose credibility and their customers' confidence.
Needless to say, businesses must improve the protection of their infrastructures and networks against cyber attacks.
Fortunately, the cybersecurity space has been continually working on developments to keep pace with evolving threats. Here are five tools that businesses should consider adding to their arsenal to boost their defenses.
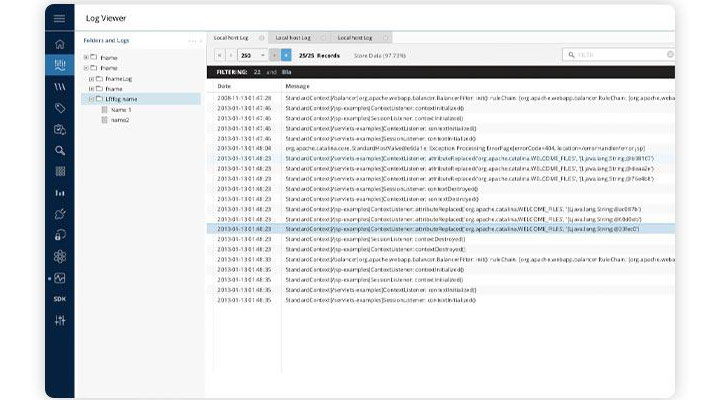
Companies must know what is exactly happening within their infrastructures. Fortunately, computers and digital devices have logging mechanisms built in that record most, if not all, computing processes that transpire within them. Logs can reveal patterns and trends that can be indicative of a security breach or malware infestation.
However, since log files are essentially dumps of information stored in plain text format, performing log analyses manually can be a painstaking process.
A way to effectively tap into logs is by using a log analysis tool like XpoLog. The solution collects log files from sources such as servers, endpoints, and applications in real-time.
Using artificial intelligence (AI), it then parses and analyzes the information contained in these logs in order to identify alarming patterns. Insights generated from the analysis can readily inform administrators of any problems that warrant attention.
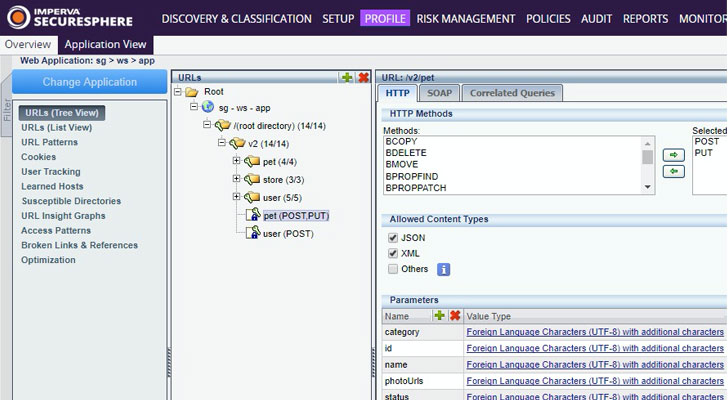
Attackers are constantly probing infrastructures, so it's critical to have mechanisms that immediately prevent malicious traffic from accessing key network resources such as web applications and databases.
This can be done through the use of web application firewalls (WAFs) and data protection services.
Imperva has been a leading name in WAF and distributed denial-of-service (DDoS) attack mitigation. Most organizations now maintain hybrid infrastructures consisting of on-premises devices and cloud components such as instances, storage, and data warehouses.
Imperva's WAF can be deployed to protect these resources. It profiles traffic and transactions conducted and prevents malicious traffic and actions from accessing these components.
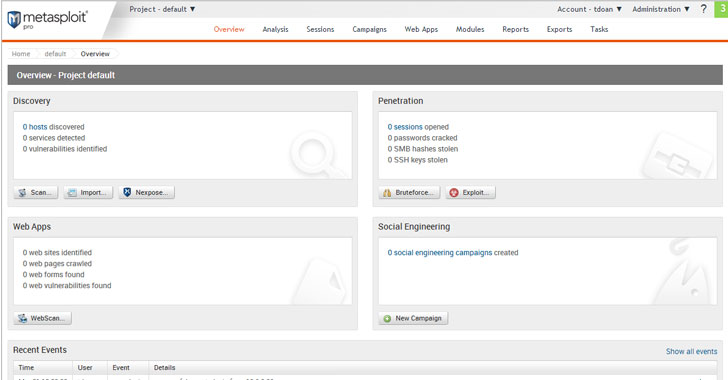
Companies shouldn't wait for actual cyber attacks to happen to find out if their solutions are properly implemented. They can be proactive about and test their defenses themselves.
Administrators can perform penetration testing by using frameworks such as Metasploit. It's an open source tool that can be configured to scan for exploits and even deploy a payload to vulnerable systems.
Metasploit also features select evasion tools that could potentially circumvent existing security measures. It can be used on Windows, Linux, and Mac OS X systems.
Discovering gaps in security gives companies a chance to remedy these issues before an actual attack actually strikes.
The human element continues to be the biggest vulnerability in a company's cybersecurity chain.
Over 90 percent of security breaches are found to be caused by human error. This is why cybercriminals still actively employ social engineering attacks such as phishing to try and compromise infrastructures.
Such attacks trick users into giving up their credentials or installing malware into their systems.
HoxHunt addresses this by teaching users how to check if an email is a phishing message or if a website is malicious.
Companies can train users using simulated phishing attacks. Hoxhunt's AI-driven engine even personalizes these attacks to copy how real-world attacks look like.
Users can report these attacks through a special plugin, and they get immediate feedback on how well they've performed.
Not all attacks seek to breach and steal information from companies. Businesses also have to be wary of fraud attacks.
Hackers and fraudsters now have access to millions of valid personal and financial information from previous data breaches that they can easily manipulate business' e-commerce channels, costing merchants billions of dollars globally.
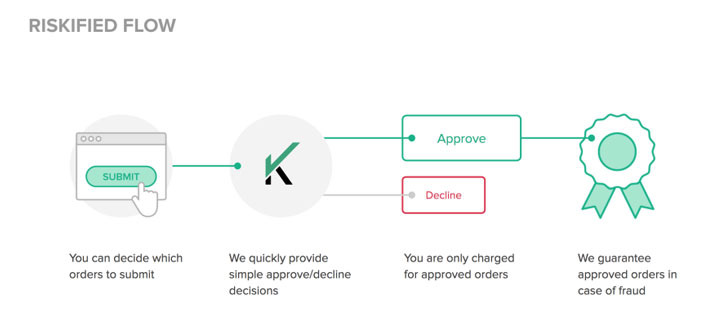
Solutions like Riskified offer comprehensive means to prevent online fraud throughout the course of an online transaction.
Riskified uses machine learning to analyze each transaction and only allows legitimate orders to be processed. It also provides a dynamic checkout feature that automatically adjusts based on a customer's risk profile, providing various means for customers to verify their purchases.
For instance, a customer with a higher risk profile may be asked to perform additional verification steps without denying transactions outright.
An effective cybersecurity strategy demands that businesses cover all possible areas that can be exploited by attackers. This requires adopting a comprehensive set of tools and solutions that would keep their infrastructures secure. Implementing and integrating these solutions do require spending.
But considering the costs that falling victim to cyberattacks bring, it's only prudent to make these investments. It's simply the reality of doing business in this highly digital landscape.
Businesses, in particular, have become prime targets for cybercriminals due to the nature of data and information they process and store.
2018 saw a slew of data breaches targeting large enterprises that resulted in the theft of the personal and financial records of millions of customers.
Falling victim to cyber attacks can deal with a major financial blow to businesses as the cost of dealing with an attack has risen to $1.1 million on the average. It can even be more devastating for small to medium-sized businesses.
60 percent of these smaller operations close within six months after failing to recover from cyber attacks. But aside from these monetary costs, companies can also lose credibility and their customers' confidence.
Needless to say, businesses must improve the protection of their infrastructures and networks against cyber attacks.
Fortunately, the cybersecurity space has been continually working on developments to keep pace with evolving threats. Here are five tools that businesses should consider adding to their arsenal to boost their defenses.
Log Analysis — XpoLog
Companies must know what is exactly happening within their infrastructures. Fortunately, computers and digital devices have logging mechanisms built in that record most, if not all, computing processes that transpire within them. Logs can reveal patterns and trends that can be indicative of a security breach or malware infestation.
However, since log files are essentially dumps of information stored in plain text format, performing log analyses manually can be a painstaking process.
A way to effectively tap into logs is by using a log analysis tool like XpoLog. The solution collects log files from sources such as servers, endpoints, and applications in real-time.
Using artificial intelligence (AI), it then parses and analyzes the information contained in these logs in order to identify alarming patterns. Insights generated from the analysis can readily inform administrators of any problems that warrant attention.
Application and Data Protection — Imperva
Attackers are constantly probing infrastructures, so it's critical to have mechanisms that immediately prevent malicious traffic from accessing key network resources such as web applications and databases.
This can be done through the use of web application firewalls (WAFs) and data protection services.
Imperva has been a leading name in WAF and distributed denial-of-service (DDoS) attack mitigation. Most organizations now maintain hybrid infrastructures consisting of on-premises devices and cloud components such as instances, storage, and data warehouses.
Imperva's WAF can be deployed to protect these resources. It profiles traffic and transactions conducted and prevents malicious traffic and actions from accessing these components.
Penetration Testing — Metasploit
Integrating security tools into the infrastructure is one thing; checking if they actually work is another.Companies shouldn't wait for actual cyber attacks to happen to find out if their solutions are properly implemented. They can be proactive about and test their defenses themselves.
Administrators can perform penetration testing by using frameworks such as Metasploit. It's an open source tool that can be configured to scan for exploits and even deploy a payload to vulnerable systems.
Metasploit also features select evasion tools that could potentially circumvent existing security measures. It can be used on Windows, Linux, and Mac OS X systems.
Discovering gaps in security gives companies a chance to remedy these issues before an actual attack actually strikes.
Anti-Phishing — Hoxhunt
The human element continues to be the biggest vulnerability in a company's cybersecurity chain.
Over 90 percent of security breaches are found to be caused by human error. This is why cybercriminals still actively employ social engineering attacks such as phishing to try and compromise infrastructures.
Such attacks trick users into giving up their credentials or installing malware into their systems.
HoxHunt addresses this by teaching users how to check if an email is a phishing message or if a website is malicious.
Companies can train users using simulated phishing attacks. Hoxhunt's AI-driven engine even personalizes these attacks to copy how real-world attacks look like.
Users can report these attacks through a special plugin, and they get immediate feedback on how well they've performed.
Fraud Detection — Riskified
Not all attacks seek to breach and steal information from companies. Businesses also have to be wary of fraud attacks.
Hackers and fraudsters now have access to millions of valid personal and financial information from previous data breaches that they can easily manipulate business' e-commerce channels, costing merchants billions of dollars globally.
Solutions like Riskified offer comprehensive means to prevent online fraud throughout the course of an online transaction.
Riskified uses machine learning to analyze each transaction and only allows legitimate orders to be processed. It also provides a dynamic checkout feature that automatically adjusts based on a customer's risk profile, providing various means for customers to verify their purchases.
For instance, a customer with a higher risk profile may be asked to perform additional verification steps without denying transactions outright.
Investments Required
An effective cybersecurity strategy demands that businesses cover all possible areas that can be exploited by attackers. This requires adopting a comprehensive set of tools and solutions that would keep their infrastructures secure. Implementing and integrating these solutions do require spending.
But considering the costs that falling victim to cyberattacks bring, it's only prudent to make these investments. It's simply the reality of doing business in this highly digital landscape.
Have something to say about this article? Comment below or share it with us on Facebook, Twitter or our LinkedIn Group.