A popular gaming platform used by hundreds of millions of people worldwide has been found vulnerable to multiple security flaws that could have allowed remote hackers to takeover players' accounts and steal sensitive data.
The vulnerabilities in question reside in the "Origin" digital distribution platform developed by Electronic Arts (EA)—the world's second-largest gaming company with over 300 million users—that allows users to purchase and play some of the most popular video games including Battlefield, Apex Legends, Madden NFL, and FIFA.
The Origin platform also manages users EA Games account authentication and allows them to find friends, join games, and manage their profiles.
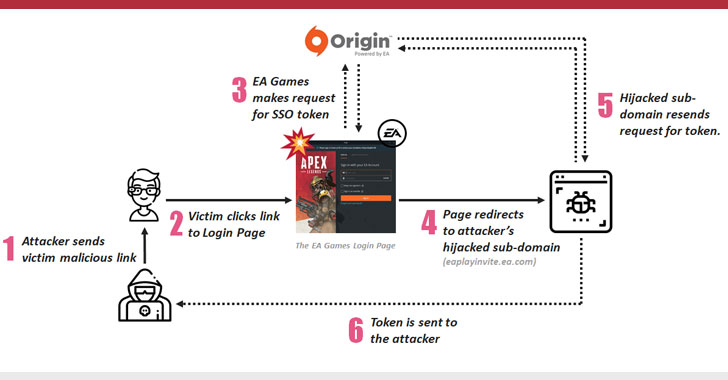
Discovered by researchers at Check Point and CyberInt, the vulnerabilities when chained together could have allowed attackers to hijack gamer's EA account just by convincing them into opening an official webpage from the EA Games website.
To perform this attack, as shown in the video demonstration, researchers took advantage of a long-known unpatched weakness in Microsoft's Azure cloud service that allowed them to takeover one of the EA subdomains, which was previously registered with Azure to host one of the Origin's services.
As explained in a previous report, if DNS (CNAME) of a domain/subdomain is pointing to Azure cloud platform but has not been configured or linked to an active Azure account, any other Azure user can hijack it to park that subdomain to his/her Azure server.
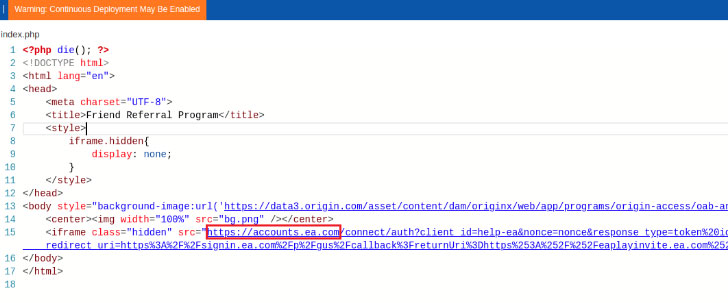
In their proof-of-concept attack, researchers hijacked "eaplayinvite.ea.com" and hosted a script on it that exploited weaknesses in the EA games' oAuth single sign-on (SSO) and TRUST mechanism.
The webpage eventually allowed the researchers to capture players secret SSO tokens just by convincing them into visiting it in the same web browser where they already have an active session on the EA website and takeover their accounts without requiring actual credentials.
In a worst-case scenario, CheckPoint researchers said an attacker could have exploited these flaws to cause potential damage like gaining access to players' credit card information with the ability to fraudulently purchase in-game currency on behalf of the players.
CyberInt and Check Point immediately reported their findings to EA Games and helped the company fix the security loopholes to protect their gaming customers. The security firm went public with its findings today—almost three months after EA addressed the issues.
The vulnerabilities in question reside in the "Origin" digital distribution platform developed by Electronic Arts (EA)—the world's second-largest gaming company with over 300 million users—that allows users to purchase and play some of the most popular video games including Battlefield, Apex Legends, Madden NFL, and FIFA.
The Origin platform also manages users EA Games account authentication and allows them to find friends, join games, and manage their profiles.
Discovered by researchers at Check Point and CyberInt, the vulnerabilities when chained together could have allowed attackers to hijack gamer's EA account just by convincing them into opening an official webpage from the EA Games website.
To perform this attack, as shown in the video demonstration, researchers took advantage of a long-known unpatched weakness in Microsoft's Azure cloud service that allowed them to takeover one of the EA subdomains, which was previously registered with Azure to host one of the Origin's services.
"During Cyber Int's research, though, [it] found that the ea-invite-reg.azurewebsites.net service was not in-use anymore within Azure cloud services; however, the unique subdomain eaplayinvite.ea.com still redirect to it using the CNAME configuration," CheckPoint researchers said in a report published today.
In their proof-of-concept attack, researchers hijacked "eaplayinvite.ea.com" and hosted a script on it that exploited weaknesses in the EA games' oAuth single sign-on (SSO) and TRUST mechanism.
The webpage eventually allowed the researchers to capture players secret SSO tokens just by convincing them into visiting it in the same web browser where they already have an active session on the EA website and takeover their accounts without requiring actual credentials.
"The TRUST mechanism exists between ea.com and origin.com domains and their subdomains. Successfully abusing the mechanism enabled our research team to manipulate the OAuth protocol implementation for full account takeover exploitation," researchers explained.
In a worst-case scenario, CheckPoint researchers said an attacker could have exploited these flaws to cause potential damage like gaining access to players' credit card information with the ability to fraudulently purchase in-game currency on behalf of the players.
CyberInt and Check Point immediately reported their findings to EA Games and helped the company fix the security loopholes to protect their gaming customers. The security firm went public with its findings today—almost three months after EA addressed the issues.
Have something to say about this article? Comment below or share it with us on Facebook, Twitter or our LinkedIn Group.