Insecure Internet-connected devices have aided different types of cybercrime for years, most common being DDoS and spam campaigns. But cybercriminals have now shifted toward a profitable scheme where botnets do not just launch DDoS or spam—they mine cryptocurrencies as well.
Smominru, an infamous cryptocurrency-mining and credential-stealing botnet, has become one of the rapidly spreading computer viruses that is now infecting over 90,000 machines each month around the world.
Though the campaigns that are hacking computers with the Smominru botnet have not been designed to go after targets with any specific interest, the latest report from Guardicore Labs researchers shed light on the nature of the victims and the attack infrastructure.
According to the researchers, just last month, more than 4,900 networks were infected by the worm without any discrimination, and many of these networks had dozens of internal machines infected.
Infected networks include US-based higher-education institutions, medical firms, and even cybersecurity companies, with the largest network belonging to a healthcare provider in Italy with a total of 65 infected hosts.
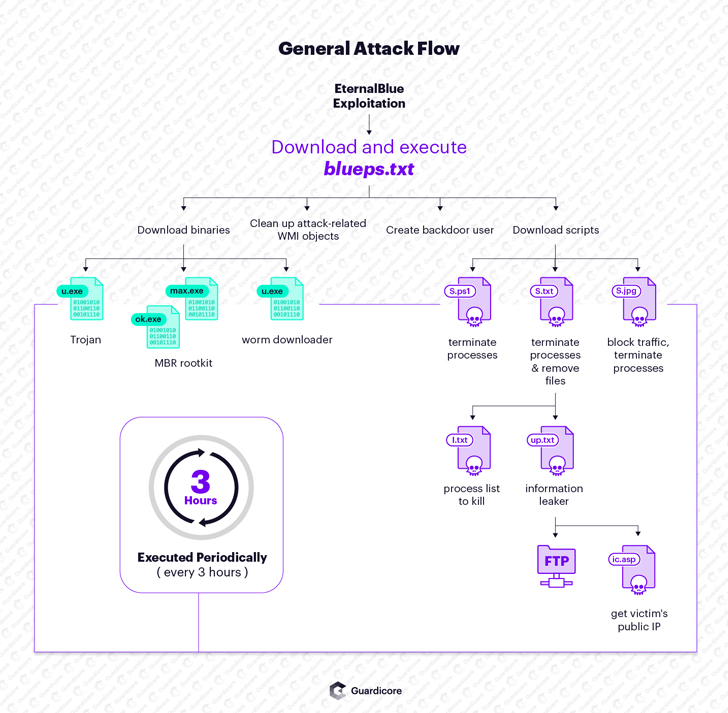
Active since 2017, Smominru botnet compromises Windows machines primarily using EternalBlue, an exploit that was created by the U.S. National Security Agency but later got leaked to the public by the Shadow Brokers hacking group and then most famously used by the hard-hitting WannaCry ransomware attack in 2016.
The botnet has also been designed to gain initial access on vulnerable systems by simply brute-forcing weak credentials for different Windows services, including MS-SQL, RDP, and Telnet.
Once gaining initial access to the targeted systems, Smominru installs a Trojan module and a cryptocurrency miner and propagates inside the network to harness CPU power of victims' PCs to mine Monero and send it to a wallet owned by the malware's operator.
A month ago, it was also revealed that the operators behind the botnet upgraded Smominru to add a data harvesting module and Remote Access Trojan (RAT) to their botnet's cryptocurrency mining code.
The latest variant of Smominru downloads and runs at least 20 distinct malicious scripts and binary payloads, including a worm downloader, a Trojan horse and an MBR rootkit.
According to the new report, Guardicore Labs researchers said they managed to gain access to one of the attackers' core servers, which stores victim information and their stolen credentials, and took a closer look at the nature of the victims.
"Guardicore Labs has informed identifiable victims and provided them with the details of their infected machines."
The botnet is infecting vulnerable machines—the majority of which are running Windows 7 and Windows Server 2008—at a rate of 4,700 machines per day with several thousands of infections detected in countries including China, Taiwan, Russia, Brazil, and the U.S.
Majority of the infected machines discovered were primarily small servers, with 1-4 CPU cores, leaving most of them unusable due to overutilization of their CPUs with the mining process.
Analysis by the researchers also revealed that one-fourth of the Smominru victims was reinfected by the worm, suggesting that they "attempted to clean up their systems without fixing the root cause issue that left them vulnerable in the first place."
Unlike previous variants of Smominru, the new variant also removes infections from compromised systems, if any, that are added by other cyber-criminal groups, along with blocking TCP ports (SMB, RPC) in an attempt to prevent other attackers from breaching its infected machines.
Guardicore researchers have also released a complete list of IoCs (indicators of compromise) and a free Powershell script on GitHub that you can run from your Windows command-line interface to check if your system is infected with the Smominru worm or not.
Since the Smominru worm leverages the EternalBlue exploit and weak passwords, users are advised to keep their systems and software updated and stick to strong, complex and unique passwords to avoid being a victim of such threats.
Besides this, for an organization, it is also essential to have additional security measures, such as "applying network segmentation and minimizing the number of internet-facing servers.
Smominru, an infamous cryptocurrency-mining and credential-stealing botnet, has become one of the rapidly spreading computer viruses that is now infecting over 90,000 machines each month around the world.
Though the campaigns that are hacking computers with the Smominru botnet have not been designed to go after targets with any specific interest, the latest report from Guardicore Labs researchers shed light on the nature of the victims and the attack infrastructure.
According to the researchers, just last month, more than 4,900 networks were infected by the worm without any discrimination, and many of these networks had dozens of internal machines infected.
Infected networks include US-based higher-education institutions, medical firms, and even cybersecurity companies, with the largest network belonging to a healthcare provider in Italy with a total of 65 infected hosts.
Active since 2017, Smominru botnet compromises Windows machines primarily using EternalBlue, an exploit that was created by the U.S. National Security Agency but later got leaked to the public by the Shadow Brokers hacking group and then most famously used by the hard-hitting WannaCry ransomware attack in 2016.
The botnet has also been designed to gain initial access on vulnerable systems by simply brute-forcing weak credentials for different Windows services, including MS-SQL, RDP, and Telnet.
Once gaining initial access to the targeted systems, Smominru installs a Trojan module and a cryptocurrency miner and propagates inside the network to harness CPU power of victims' PCs to mine Monero and send it to a wallet owned by the malware's operator.
A month ago, it was also revealed that the operators behind the botnet upgraded Smominru to add a data harvesting module and Remote Access Trojan (RAT) to their botnet's cryptocurrency mining code.
The latest variant of Smominru downloads and runs at least 20 distinct malicious scripts and binary payloads, including a worm downloader, a Trojan horse and an MBR rootkit.
"The attackers create many backdoors on the machine in different phases of the attack. These include newly-created users, scheduled tasks, WMI objects and services set to run at boot time," the researchers say.
According to the new report, Guardicore Labs researchers said they managed to gain access to one of the attackers' core servers, which stores victim information and their stolen credentials, and took a closer look at the nature of the victims.
"The attackers' logs describe each infected host; they include its external and internal IP addresses, the operating system it runs and even the load on the system's CPU(s). Furthermore, the attackers attempt to collect the running processes and steal credentials using Mimikatz," the researchers say.
"Guardicore Labs has informed identifiable victims and provided them with the details of their infected machines."
The botnet is infecting vulnerable machines—the majority of which are running Windows 7 and Windows Server 2008—at a rate of 4,700 machines per day with several thousands of infections detected in countries including China, Taiwan, Russia, Brazil, and the U.S.
Majority of the infected machines discovered were primarily small servers, with 1-4 CPU cores, leaving most of them unusable due to overutilization of their CPUs with the mining process.
Analysis by the researchers also revealed that one-fourth of the Smominru victims was reinfected by the worm, suggesting that they "attempted to clean up their systems without fixing the root cause issue that left them vulnerable in the first place."
Unlike previous variants of Smominru, the new variant also removes infections from compromised systems, if any, that are added by other cyber-criminal groups, along with blocking TCP ports (SMB, RPC) in an attempt to prevent other attackers from breaching its infected machines.
Guardicore researchers have also released a complete list of IoCs (indicators of compromise) and a free Powershell script on GitHub that you can run from your Windows command-line interface to check if your system is infected with the Smominru worm or not.
Since the Smominru worm leverages the EternalBlue exploit and weak passwords, users are advised to keep their systems and software updated and stick to strong, complex and unique passwords to avoid being a victim of such threats.
Besides this, for an organization, it is also essential to have additional security measures, such as "applying network segmentation and minimizing the number of internet-facing servers.
Have something to say about this article? Comment below or share it with us on Facebook, Twitter or our LinkedIn Group.