An alarming security vulnerability has been discovered in several models of Android smartphones manufactured by Google, Samsung, and others that could allow malicious apps to secretly take pictures and record videos — even when they don't have specific device permissions to do so.
You must already know that the security model of the Android mobile operating system is primarily based on device permissions where each app needs to explicitly define which services, device capabilities, or user information it wants to access.
However, researchers at Checkmarx discovered that a vulnerability, tracked as CVE-2019-2234, in pre-installed camera apps on millions of devices could be leveraged by attackers to bypass such restrictions and access device camera and microphone without any permissions to do so.
The attack scenario involves a rogue app that only needs access to device storage (i.e., SD card), which is one of the most common requested permissions and does not raise any suspicion.
According to researchers, by merely manipulating specific "actions and intents," a malicious app can trick vulnerable camera apps into performing actions on behalf of the attacker, who can then steal photos and videos from the device storage after being taken.
Since smartphone camera apps already have access to required permissions, the flaw could allow attackers to indirectly and surreptitiously take photos, record videos, eavesdrop on conversations, and track location — even if the phone is locked, the screen is off, or the app is closed.
To demonstrate the risk of the vulnerability for Android users, the researchers created a proof-of-concept rogue app masqueraded as an innocent weather app that only asks for the basic storage permission.
The PoC app came in two parts — the client app running on an Android device and an attacker's controlled command-and-control (C&C) server that the app creates a persistent connection to so that closing the app did not terminate the server connection.
The malicious app designed by the researchers was able to perform a long list of malicious tasks, including:
The malicious app implemented the wait for a voice call option via the phone's proximity sensor that can sense when the phone is held to the victim's ear.
Researchers have also published a video of successfully exploiting the vulnerabilities on Google Pixel 2 XL and Pixel 3 and confirmed that the vulnerabilities were relevant to all Google phone models.
The Checkmarx research team responsibly reported their findings to Google in early July with the PoC app and a video demonstrating an attack scenario.
Google confirmed and addressed the vulnerability in its Pixel line of devices with a camera update that became available in July, and contacted other Android-based smartphone OEMs in late August to inform them about the issue, which the company rated as "High" in severity.
However, Google did not disclose the names of the affected manufacturers and models.
"We appreciate Checkmarx bringing this to our attention and working with Google and Android partners to coordinate disclosure," Google said.
"The issue was addressed on impacted Google devices via a Play Store update to the Google Camera Application in July 2019. A patch has also been made available to all partners."
Checkmarx also reported the vulnerability to Samsung that affected its Camera app. Samsung confirmed and fixed the issue in late August, although it wasn't revealed when the company patched the flaw.
To protect yourself from attacks surrounding this vulnerability, ensure you are running the latest version of the camera app on your Android smartphone.
Besides this, you are also recommended to run the latest version of the Android operating system and regularly update apps installed on your phone.
You must already know that the security model of the Android mobile operating system is primarily based on device permissions where each app needs to explicitly define which services, device capabilities, or user information it wants to access.
However, researchers at Checkmarx discovered that a vulnerability, tracked as CVE-2019-2234, in pre-installed camera apps on millions of devices could be leveraged by attackers to bypass such restrictions and access device camera and microphone without any permissions to do so.
How Can Attackers Exploit the Camera App Vulnerability?
The attack scenario involves a rogue app that only needs access to device storage (i.e., SD card), which is one of the most common requested permissions and does not raise any suspicion.
According to researchers, by merely manipulating specific "actions and intents," a malicious app can trick vulnerable camera apps into performing actions on behalf of the attacker, who can then steal photos and videos from the device storage after being taken.
Since smartphone camera apps already have access to required permissions, the flaw could allow attackers to indirectly and surreptitiously take photos, record videos, eavesdrop on conversations, and track location — even if the phone is locked, the screen is off, or the app is closed.
"After a detailed analysis of the Google Camera app, our team found that by manipulating specific actions and intents, an attacker can control the app to take photos and/or record videos through a rogue application that has no permissions to do so," Checkmarx wrote in a blog post published today.
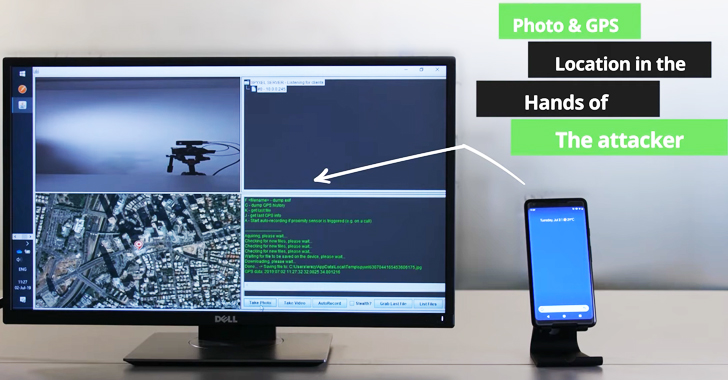
"Additionally, we found that certain attack scenarios enable malicious actors to circumvent various storage permission policies, giving them access to stored videos and photos, as well as GPS metadata embedded in photos, to locate the user by taking a photo or video and parsing the proper EXIF data. This same technique also applied to Samsung's Camera app."
To demonstrate the risk of the vulnerability for Android users, the researchers created a proof-of-concept rogue app masqueraded as an innocent weather app that only asks for the basic storage permission.
The PoC app came in two parts — the client app running on an Android device and an attacker's controlled command-and-control (C&C) server that the app creates a persistent connection to so that closing the app did not terminate the server connection.
The malicious app designed by the researchers was able to perform a long list of malicious tasks, including:
- Making the camera app on the victim's phone to take photos and record videos and then upload (retrieve) it to the C&C server.
- Pulling GPS metadata embedded into photos and videos stored on the phone to locate the user.
- Waiting for a voice call and automatically recording audio from both sides of the conversation and video from the victim's side.
- Operating in stealth mode while taking photos and recording videos, so no camera shutter sounds for alerting the user.
The malicious app implemented the wait for a voice call option via the phone's proximity sensor that can sense when the phone is held to the victim's ear.
Researchers have also published a video of successfully exploiting the vulnerabilities on Google Pixel 2 XL and Pixel 3 and confirmed that the vulnerabilities were relevant to all Google phone models.
Vulnerability Disclosure and Patch Availability
The Checkmarx research team responsibly reported their findings to Google in early July with the PoC app and a video demonstrating an attack scenario.
Google confirmed and addressed the vulnerability in its Pixel line of devices with a camera update that became available in July, and contacted other Android-based smartphone OEMs in late August to inform them about the issue, which the company rated as "High" in severity.
However, Google did not disclose the names of the affected manufacturers and models.
"We appreciate Checkmarx bringing this to our attention and working with Google and Android partners to coordinate disclosure," Google said.
"The issue was addressed on impacted Google devices via a Play Store update to the Google Camera Application in July 2019. A patch has also been made available to all partners."
Also Read: Over 1,300 Android Apps Caught Collecting Data Even If You Deny Permissions
Checkmarx also reported the vulnerability to Samsung that affected its Camera app. Samsung confirmed and fixed the issue in late August, although it wasn't revealed when the company patched the flaw.
"Since being notified of this issue by Google, we have subsequently released patches to address all Samsung device models that may be affected. We value our partnership with the Android team that allowed us to identify and address this matter directly," Samsung said.
To protect yourself from attacks surrounding this vulnerability, ensure you are running the latest version of the camera app on your Android smartphone.
Besides this, you are also recommended to run the latest version of the Android operating system and regularly update apps installed on your phone.
Have something to say about this article? Comment below or share it with us on Facebook, Twitter or our LinkedIn Group.