Here's excellent news for sysadmins. You can now use a physical security key as hardware-based two-factor authentication to securely log into a remote system via SSH protocol.
OpenSSH, one of the most widely used open-source implementations of the Secure Shell (SSH) Protocol, yesterday announced the 8.2 version of the software that primarily includes two new significant security enhancements.
First, OpenSSH 8.2 added support for FIDO/U2F hardware authenticators, and the second, it has deprecated SSH-RSA public key signature algorithm and planned to disable it by default in the future versions of the software.
FIDO (Fast Identity Online) protocol based hardware security devices are stronger and fool-proof mechanisms for authentication because it enables public-key cryptography to protect against advanced malware, phishing, and man-in-the-middle attacks.
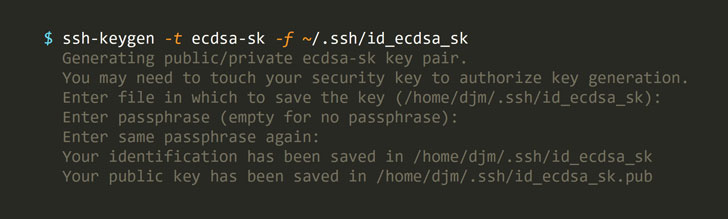
"In OpenSSH, FIDO devices are supported by new public key types' ecdsa-sk' and 'ed25519-sk', along with corresponding certificate types," the OpenSSH 8.2 release note says.
"FIDO tokens are most commonly connected via USB but may be attached via other means such as Bluetooth or NFC. In OpenSSH, communication with the token is managed via a middleware library."
OpenSSH team first introduced the support for U2F/FIDO as an experimental feature in November 2019, which relied on the same middleware for Yubico's libfido2 that is capable of talking to any standard USB HID U2F or FIDO2 token.
A physical security key adds an extra layer of authentication to an account on top of your password, and users can quickly log into their accounts securely just by inserting the USB security key and pressing a button.
That means, even if attackers manage to infect your computer or somehow steal your SSH password, they would not be able to access the remote system over SSH without presenting the physical security key.
Besides this, the announcement to deprecate SSH-RSA public key signature algorithm is also significant because SHA-1 hash algorithm is slow and potentially insecure that can be cracked easily using fewer resources than ever before.
"This algorithm is unfortunately still used widely despite the existence of better alternatives, being the only remaining public-key signature algorithm specified by the original SSH RFCs."
"A future release of OpenSSH will enable UpdateHostKeys by default to allow the client to automatically migrate to better algorithms. Users may consider enabling this option manually."
If you are unaware, OpenSSH last year also introduced another security feature that encrypts private keys before storing them into the system memory, protecting it against almost all types of side-channel attacks.
You can find more information about the latest release and guide on how to generate hardware security keys with OpenSSH in the release notes.
OpenSSH, one of the most widely used open-source implementations of the Secure Shell (SSH) Protocol, yesterday announced the 8.2 version of the software that primarily includes two new significant security enhancements.
First, OpenSSH 8.2 added support for FIDO/U2F hardware authenticators, and the second, it has deprecated SSH-RSA public key signature algorithm and planned to disable it by default in the future versions of the software.
FIDO (Fast Identity Online) protocol based hardware security devices are stronger and fool-proof mechanisms for authentication because it enables public-key cryptography to protect against advanced malware, phishing, and man-in-the-middle attacks.
"In OpenSSH, FIDO devices are supported by new public key types' ecdsa-sk' and 'ed25519-sk', along with corresponding certificate types," the OpenSSH 8.2 release note says.
"FIDO tokens are most commonly connected via USB but may be attached via other means such as Bluetooth or NFC. In OpenSSH, communication with the token is managed via a middleware library."
OpenSSH team first introduced the support for U2F/FIDO as an experimental feature in November 2019, which relied on the same middleware for Yubico's libfido2 that is capable of talking to any standard USB HID U2F or FIDO2 token.
A physical security key adds an extra layer of authentication to an account on top of your password, and users can quickly log into their accounts securely just by inserting the USB security key and pressing a button.
That means, even if attackers manage to infect your computer or somehow steal your SSH password, they would not be able to access the remote system over SSH without presenting the physical security key.
Besides this, the announcement to deprecate SSH-RSA public key signature algorithm is also significant because SHA-1 hash algorithm is slow and potentially insecure that can be cracked easily using fewer resources than ever before.
"This algorithm is unfortunately still used widely despite the existence of better alternatives, being the only remaining public-key signature algorithm specified by the original SSH RFCs."
"A future release of OpenSSH will enable UpdateHostKeys by default to allow the client to automatically migrate to better algorithms. Users may consider enabling this option manually."
If you are unaware, OpenSSH last year also introduced another security feature that encrypts private keys before storing them into the system memory, protecting it against almost all types of side-channel attacks.
You can find more information about the latest release and guide on how to generate hardware security keys with OpenSSH in the release notes.
Have something to say about this article? Comment below or share it with us on Facebook, Twitter or our LinkedIn Group.