A cybersecurity researcher today disclosed technical details of multiple high severity vulnerabilities he discovered in WhatsApp, which, if exploited, could have allowed remote attackers to compromise the security of billions of users in different ways.
When combined together, the reported issues could have even enabled hackers to remotely steal files from the Windows or Mac computer of a victim using the WhatsApp desktop app by merely sending a specially crafted message.
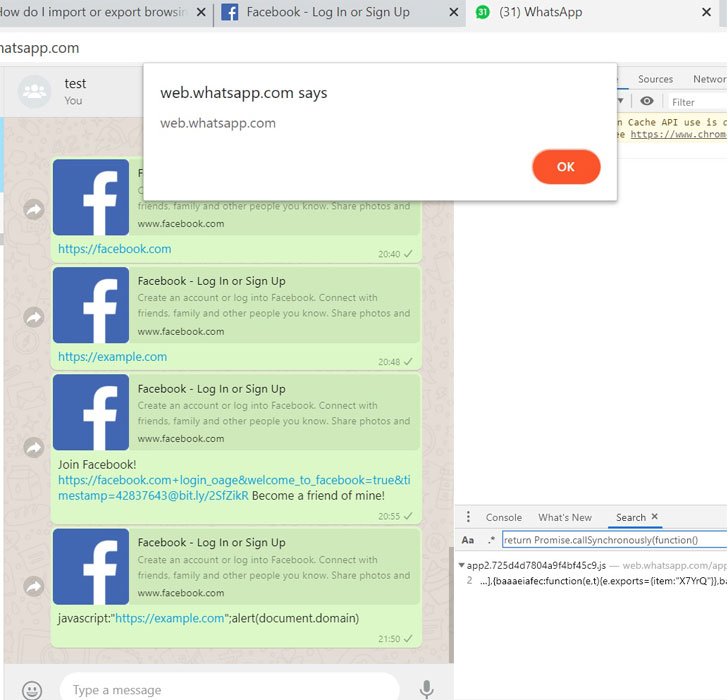
Discovered by PerimeterX researcher Gal Weizman and tracked as CVE-2019-18426, the flaws specifically resided in WhatsApp Web, a browser version of the world's most popular messaging application that also powers its Electron-based cross-platform apps for desktop operating systems.
In a blog post published today, Weizman revealed that WhatsApp Web was vulnerable to a potentially dangerous open-redirect flaw that led to persistent cross-site scripting attacks, which could have been triggered by sending a specially crafted message to the targeted WhatsApp users.
In the case when an unsuspecting victim views the malicious message over the browser, the flaw could have allowed attackers to execute arbitrary code in the context of WhatsApp's web domain.
Whereas, when viewed through the vulnerable desktop application, the malicious code runs on the recipients' systems in the context of the vulnerable application.
Moreover, the misconfigured content security policy on the WhatsApp web domain also allowed the researcher to load XSS payloads of any length using an iframe from a separate attacker-controlled website on the Internet.
"If the CSP rules were well configured, the power gained by this XSS would have been much smaller. Being able to bypass the CSP configuration allows an attacker to steal valuable information from the victim, load external payloads easily, and much more," the researcher said.
As shown in the screenshot above, Weizman demonstrated the remote file read attack over WhatsApp by accessing the content of the hosts file from a victim's computer.
Besides this, the open-redirect flaw could have had also been used to manipulate URL banners, a preview of the domain WhatsApp displays to the recipients when they receive a message containing links, and trick users into falling for phishing attacks.
Weizman responsibly reported these issues to the Facebook security team last year, who then patched the flaws, released an updated version of its desktop application, and also rewarded Weizman with $12,500 under the company's bug bounty program.
When combined together, the reported issues could have even enabled hackers to remotely steal files from the Windows or Mac computer of a victim using the WhatsApp desktop app by merely sending a specially crafted message.
Discovered by PerimeterX researcher Gal Weizman and tracked as CVE-2019-18426, the flaws specifically resided in WhatsApp Web, a browser version of the world's most popular messaging application that also powers its Electron-based cross-platform apps for desktop operating systems.
In a blog post published today, Weizman revealed that WhatsApp Web was vulnerable to a potentially dangerous open-redirect flaw that led to persistent cross-site scripting attacks, which could have been triggered by sending a specially crafted message to the targeted WhatsApp users.
In the case when an unsuspecting victim views the malicious message over the browser, the flaw could have allowed attackers to execute arbitrary code in the context of WhatsApp's web domain.
Whereas, when viewed through the vulnerable desktop application, the malicious code runs on the recipients' systems in the context of the vulnerable application.
Moreover, the misconfigured content security policy on the WhatsApp web domain also allowed the researcher to load XSS payloads of any length using an iframe from a separate attacker-controlled website on the Internet.
"If the CSP rules were well configured, the power gained by this XSS would have been much smaller. Being able to bypass the CSP configuration allows an attacker to steal valuable information from the victim, load external payloads easily, and much more," the researcher said.
As shown in the screenshot above, Weizman demonstrated the remote file read attack over WhatsApp by accessing the content of the hosts file from a victim's computer.
Besides this, the open-redirect flaw could have had also been used to manipulate URL banners, a preview of the domain WhatsApp displays to the recipients when they receive a message containing links, and trick users into falling for phishing attacks.
Weizman responsibly reported these issues to the Facebook security team last year, who then patched the flaws, released an updated version of its desktop application, and also rewarded Weizman with $12,500 under the company's bug bounty program.
Have something to say about this article? Comment below or share it with us on Facebook, Twitter or our LinkedIn Group.