Phishing attacks have become one of the business world's top cybersecurity concerns. These social engineering attacks have been rising over the years, with the most recent report from the Anti-Phishing Working Group coalition identifying over 266,000 active spoofed websites, which is nearly double the number detected during Q4 2018.
Hackers have evolved their methods, from regular phishing attacks to spear phishing, where they use email messages disguised as coming from legitimate sources to dupe specific individuals.
This is why the global spear phishing protection software market is estimated to reach $1.8 billion by 2025.
However, conventional defenses can still fall short due to one particular weakness in the security perimeter – the human factor. Indeed, some 33 percent of 2019's data breaches involved humans falling victim to social engineering attacks. And given how sophisticated and creative the phishing perpetrators have been getting, it's easy to see how even the most tech-savvy among us can become victims.
"Typically, information security departments have two problems: technology and human factors," says Mika Aalto, the CEO of phishing training software company Hoxhunt. "One can have the best technology protecting their assets, but if an employee falls into a social engineering trap, it could jeopardize the efforts of keeping the organization safe from cybercriminals."
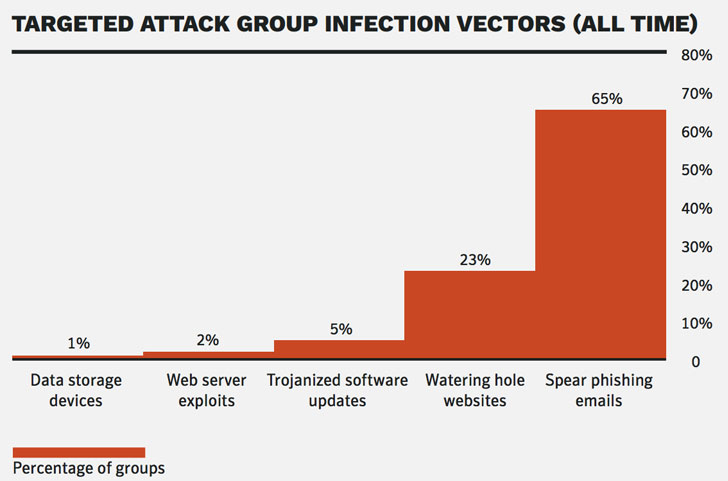
Targeting specific people with messages cleverly disguised to appear as legitimate, spear-phishing attacks trick users into opening attachments to execute malware, or clicking links that lead to bogus websites designed to steal information. According to a Symantec report, 65 percent of all targeted attacks have involved spear-phishing, making it by far the most common form of attack.
Attackers now have a variety of weapons in their arsenal to execute their spear-phishing campaigns and whatever other tactics they might want to try on for size. Massive botnets are now available either directly or for hire that would allow them to distribute scams to millions of potential targets.
Attackers are now also leveraging artificial intelligence (AI) to launch more potent attacks. They now use language processing, data scraping, and automation to instantly create realistic emails that are highly personalized and even use today's common vocabulary and syntax.
This increasing sophistication enables spear-phishing emails and messages to circumvent conventional defenses like spam filters.
Organizations are investing heavily on enterprise-grade security solutions to cover most potential vectors of attack such as endpoint security tools, firewalls, spam filters, and attack simulation and testing platforms. But regardless of these increasing investments, many infrastructures continue to be vulnerable due to human fallibility.
According to Kaspersky, a software vendor, negligence of staff is the second most likely cause of a data breach, second only to malware. For example, some employees tend to overlook the importance of updating their workstations' operating systems and software.
This exposes their organization's infrastructure to hackers who can easily exploit unpatched vulnerabilities. Employees also continue to fall for social engineering and phishing attacks by clicking on suspicious emails or following the instructions of a fraudulent request.
Since spear-phishing emails can now get past spam filters, organizations have become all the more exposed, and all team members need to maintain high levels of vigilance.
This is why Aalto sees phishing prevention as a matter of interaction and not just education. "Traditional cybersecurity training methods, such as phishing simulations, do not work because they solely focus on awareness," he says. "Instead, training should emphasize the importance of engagement.
Success highly relies on continuous learning: in an ideal world, employees frequently receive and engage with up-to-date training that prepares them for sophisticated social engineering attacks both at the workplace and in their private lives."
And without this type of preparedness, the consequences can be severe. In late 2019, Japanese media corporation Nikkei fell victim to a phishing scam when an employee transferred approximately $29 million to a cybercriminal's bank account. The scammer posed as a management executive of Nikkei and gave fraudulent instructions to an employee to make the transfer.
The widespread adoption of security tools can create a false sense of security in employees. They may be led to believe that every email or message that isn't sent to the spam folder is safe to open.
That's why automated employee training solutions are so potent when it comes to helping companies avoid falling victim to phishing attacks. Hoxhunt, for instance, can run simulated phishing campaigns that are personalized based on the user's language and location. These emails resemble the current threats in the industry.
The platform also uses AI to gather information about the organization and its members to tailor the training based on the needs of each of its users. When a user fails to report a simulated attack, they are sent bite-sized cybersecurity information and tips on how to detect threats.
In addition, employees are rewarded by the system when they report phishing emails. Staff members can also track their progress and compare it with that of their peers via a leaderboard.
By promoting awareness as well as engagement, this approach ensures that employees are equipped with the right skills and knowledge that enable them to deal with these latest threats.
The rise of spear-phishing campaigns and the growing incidents of data breaches should concern us all. Relying on conventional, tech-based security solutions to defend against various threats is not enough, especially since human error continues to be a key risk factor.
It's high time humans are considered an important cybersecurity element. However, addressing the human element is no easy feat, as it requires a change in every person's mindset.
"Only continuous learning leads to sustained behavior change that is essential to ensure that employees can defend the organization's assets," Aalto concludes. "Focusing on positive reinforcement in cybersecurity training will guarantee stronger defenses."
Hackers have evolved their methods, from regular phishing attacks to spear phishing, where they use email messages disguised as coming from legitimate sources to dupe specific individuals.
This is why the global spear phishing protection software market is estimated to reach $1.8 billion by 2025.
However, conventional defenses can still fall short due to one particular weakness in the security perimeter – the human factor. Indeed, some 33 percent of 2019's data breaches involved humans falling victim to social engineering attacks. And given how sophisticated and creative the phishing perpetrators have been getting, it's easy to see how even the most tech-savvy among us can become victims.
"Typically, information security departments have two problems: technology and human factors," says Mika Aalto, the CEO of phishing training software company Hoxhunt. "One can have the best technology protecting their assets, but if an employee falls into a social engineering trap, it could jeopardize the efforts of keeping the organization safe from cybercriminals."
The Rising Complexity of Spear Phishing
Targeting specific people with messages cleverly disguised to appear as legitimate, spear-phishing attacks trick users into opening attachments to execute malware, or clicking links that lead to bogus websites designed to steal information. According to a Symantec report, 65 percent of all targeted attacks have involved spear-phishing, making it by far the most common form of attack.
Attackers now have a variety of weapons in their arsenal to execute their spear-phishing campaigns and whatever other tactics they might want to try on for size. Massive botnets are now available either directly or for hire that would allow them to distribute scams to millions of potential targets.
Attackers are now also leveraging artificial intelligence (AI) to launch more potent attacks. They now use language processing, data scraping, and automation to instantly create realistic emails that are highly personalized and even use today's common vocabulary and syntax.
This increasing sophistication enables spear-phishing emails and messages to circumvent conventional defenses like spam filters.
Humans as the Weak Link in Cybersecurity
Organizations are investing heavily on enterprise-grade security solutions to cover most potential vectors of attack such as endpoint security tools, firewalls, spam filters, and attack simulation and testing platforms. But regardless of these increasing investments, many infrastructures continue to be vulnerable due to human fallibility.
According to Kaspersky, a software vendor, negligence of staff is the second most likely cause of a data breach, second only to malware. For example, some employees tend to overlook the importance of updating their workstations' operating systems and software.
This exposes their organization's infrastructure to hackers who can easily exploit unpatched vulnerabilities. Employees also continue to fall for social engineering and phishing attacks by clicking on suspicious emails or following the instructions of a fraudulent request.
Since spear-phishing emails can now get past spam filters, organizations have become all the more exposed, and all team members need to maintain high levels of vigilance.
This is why Aalto sees phishing prevention as a matter of interaction and not just education. "Traditional cybersecurity training methods, such as phishing simulations, do not work because they solely focus on awareness," he says. "Instead, training should emphasize the importance of engagement.
Success highly relies on continuous learning: in an ideal world, employees frequently receive and engage with up-to-date training that prepares them for sophisticated social engineering attacks both at the workplace and in their private lives."
And without this type of preparedness, the consequences can be severe. In late 2019, Japanese media corporation Nikkei fell victim to a phishing scam when an employee transferred approximately $29 million to a cybercriminal's bank account. The scammer posed as a management executive of Nikkei and gave fraudulent instructions to an employee to make the transfer.
Strengthening the Human Factor
The widespread adoption of security tools can create a false sense of security in employees. They may be led to believe that every email or message that isn't sent to the spam folder is safe to open.
That's why automated employee training solutions are so potent when it comes to helping companies avoid falling victim to phishing attacks. Hoxhunt, for instance, can run simulated phishing campaigns that are personalized based on the user's language and location. These emails resemble the current threats in the industry.
The platform also uses AI to gather information about the organization and its members to tailor the training based on the needs of each of its users. When a user fails to report a simulated attack, they are sent bite-sized cybersecurity information and tips on how to detect threats.
In addition, employees are rewarded by the system when they report phishing emails. Staff members can also track their progress and compare it with that of their peers via a leaderboard.
By promoting awareness as well as engagement, this approach ensures that employees are equipped with the right skills and knowledge that enable them to deal with these latest threats.
Developing the Right Mindset
The rise of spear-phishing campaigns and the growing incidents of data breaches should concern us all. Relying on conventional, tech-based security solutions to defend against various threats is not enough, especially since human error continues to be a key risk factor.
It's high time humans are considered an important cybersecurity element. However, addressing the human element is no easy feat, as it requires a change in every person's mindset.
"Only continuous learning leads to sustained behavior change that is essential to ensure that employees can defend the organization's assets," Aalto concludes. "Focusing on positive reinforcement in cybersecurity training will guarantee stronger defenses."
Have something to say about this article? Comment below or share it with us on Facebook, Twitter or our LinkedIn Group.