More than 200 million records containing a wide range of property-related information on US residents were left exposed on a database that was accessible on the web without requiring any password or authentication.
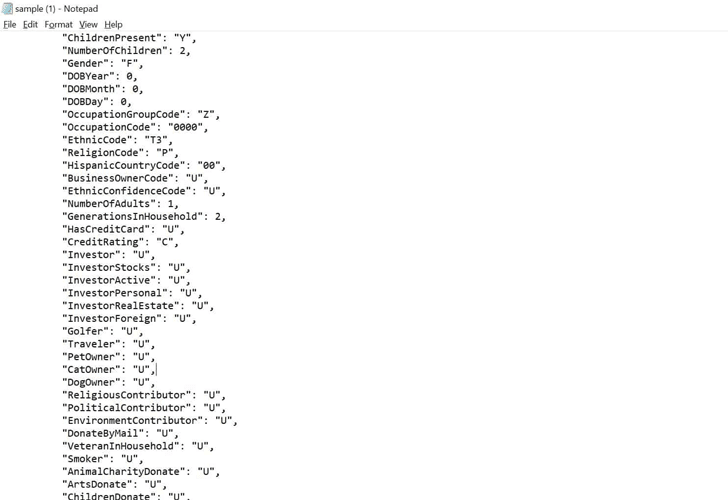
The exposed data — a mix of personal and demographic details — included the name, address, email address, age, gender, ethnicity, employment, credit rating, investment preferences, income, net worth, and property information, such as:
According to security firm Comparitech, the database, which was hosted on Google Cloud, is said to have been first indexed by search engine BinaryEdge on 26th January and discovered a day later by cybersecurity researcher Bob Diachenko.
But after failing to identify the database owner, the server was eventually taken offline more than a month later yesterday.
"We've been trying to contact Googles cloud security team (IP with database was hosted on their cloud) for them to take down the IP but never got a response," the research team told The Hacker News. "No other ways to determine the owner were possible because no reverse DNS records were available due to the cloud-based nature of the IP."
In all, the database comprised of 201,162,598 records, with each entry corresponding to a unique individual.
Comparitech noted that during the time it had access to the database, "it was being updated with new data, suggesting that the information contained is fairly recent."
Furthermore, the leak raises questions about the identity of the service that would need to store such detailed personally identifiable and demographic data of this kind.
Given that the data was not adequately secured, it's not immediately clear if other unauthorized parties accessed this database and downloaded its content. The consequence of such exposure is the increased possibility of targeted spear-phishing attacks.
"The detailed personal, demographic, and property information contained in this data-set is a gold mine for spammers, scammers, and cybercriminals who run phishing campaigns," Comparitech said. "The data allows criminals not only to target specific people but craft a more convincing message."
Specifically, attackers could target individuals with phishing emails to deliver all kinds of malware that can download malicious programs and steal sensitive information.
It's therefore crucial that users turn on two-factor authentication to add a second layer of account protection.
The incident is not the only time instances of leaky servers have drawn headlines. In recent months, Ecuadorian and Russian citizens, and US government personnel have had their personal info left unprotected on Elasticsearch servers, underscoring that there's still a long way to go when it comes to cloud security.
The exposed data — a mix of personal and demographic details — included the name, address, email address, age, gender, ethnicity, employment, credit rating, investment preferences, income, net worth, and property information, such as:
- Market value
- Property type
- Mortgage amount, rate, type, and lender
- Refinance amount, rate, type, and lender
- Previous owners
- Year built
- Number of beds and bathrooms
- Tax assessment information
According to security firm Comparitech, the database, which was hosted on Google Cloud, is said to have been first indexed by search engine BinaryEdge on 26th January and discovered a day later by cybersecurity researcher Bob Diachenko.
But after failing to identify the database owner, the server was eventually taken offline more than a month later yesterday.
"We've been trying to contact Googles cloud security team (IP with database was hosted on their cloud) for them to take down the IP but never got a response," the research team told The Hacker News. "No other ways to determine the owner were possible because no reverse DNS records were available due to the cloud-based nature of the IP."
In all, the database comprised of 201,162,598 records, with each entry corresponding to a unique individual.
Comparitech noted that during the time it had access to the database, "it was being updated with new data, suggesting that the information contained is fairly recent."
Furthermore, the leak raises questions about the identity of the service that would need to store such detailed personally identifiable and demographic data of this kind.
Spear-phishing Warning
Given that the data was not adequately secured, it's not immediately clear if other unauthorized parties accessed this database and downloaded its content. The consequence of such exposure is the increased possibility of targeted spear-phishing attacks.
"The detailed personal, demographic, and property information contained in this data-set is a gold mine for spammers, scammers, and cybercriminals who run phishing campaigns," Comparitech said. "The data allows criminals not only to target specific people but craft a more convincing message."
Specifically, attackers could target individuals with phishing emails to deliver all kinds of malware that can download malicious programs and steal sensitive information.
It's therefore crucial that users turn on two-factor authentication to add a second layer of account protection.
The incident is not the only time instances of leaky servers have drawn headlines. In recent months, Ecuadorian and Russian citizens, and US government personnel have had their personal info left unprotected on Elasticsearch servers, underscoring that there's still a long way to go when it comes to cloud security.
Have something to say about this article? Comment below or share it with us on Facebook, Twitter or our LinkedIn Group.